Web Standards and the Emerging Decentralized ID Stack
Standardization
- A Guide To Writing World Class Standards From: ETSI Type: Paper Date: 2020-07-29
- A world class standard should have well-defined objectives that respond to real needs in a timely manner.
- Its technical content should be complete and accurate.
- It should be easy to understand (or as easy as the subject matter allows!) and easy to implement.
- Its requirements should be expressed clearly and unambiguously.
- It should be validated.
- It should be well-maintained. - Trust Frameworks? Standards Matter From: Medium By: Tim Bouma Type: Post Date: 2020-11-26
- Open standards should be developed openly From: WeAreOpen By: Doug Belshaw Type: Post Date: 2021-08-19
- Premature Standardization & Interoperability From: ContinuumLoop By: Darrell O'Donnell Type: Post Date: 2022-09-11
- Trinsic Basics: What Are SSI Standards? From: Trinsic By: Anna Johnson Type: Page Date: 2020-11-12
- Manifesto: Rules for standards-makers From: Scripting.com By: Dave Winer Type: Post Date: 2017-05-08
- Why Engage with Standards? From: ContinuumLoop By: Darrell O'Donnell Type: Post Date: 2013-09-28
- Who Are the Identerati? - ForgeRock From: Forgerock Type: Post Date: 2017-03-22
- Who Runs the Internet? From: Wikipedia Type: Wiki entry Date: 2013-01-31

He points at the NIST documents about it Developing Trust Frameworks to Support Identity Federations published in 2018. He also points at the Canadian government’s definition of standards.
a document that provides a set of agreed-upon rules, guidelines or characteristics for activities or their results. Standards establish accepted practices, technical requirements, and terminologies for diverse fields.” He goes on to highlight a lot of the work being done in Canada and where it all sits relative to being a standard - “In closing, there are lots of trust frameworks being developed today. But to be truly trusted, a trust framework needs to either apply existing standards or become a standard itself.”
Open standards should be developed openly because not enough people work to ensure that equity is central to innovation and development. We believe that openness is an attitude, and one which bears fruit over time from which everyone can benefit.
5
Here’s my premise – we don’t have standards nor interoperability – at least not as people really need. We have been through a process that is powerful and good – but what we have is what I call “premature standardization.” It’s a great start but nowhere near where things will be.
There are two kinds of standards that Trinsic implements to enable interoperability and avoid vendor lock-in: data model standards and protocol standards.
I’ve used all kinds of formats and protocols in a long career as a software developer, even created a few. My new manifesto summarizes what I’ve learned about what works and what doesn’t.
too many people complain about problems but don’t step to Fix It!. There are certainly a lot of flawed standards – but they make interoperability possible – not perfect – but possible. If you haven’t used them then you have no right to complain that they are too complex, too simple (even in the same standard) or too domain specific – or any of the other rants and raves that go on.
If you’re willing to put up with a lot of work for incremental improvements then step up and join a standard. Whether that is a (relatively) fast moving standard group like OASIS (www.oasis-open.org) or a slower but more international group like ISO you will learn. You’ll also benefit from working with experts. These experts donate their time and are more than happy to provide ideas, guidance, and leadership.
You’re familiar with digital identity standards like OpenID Connect, OAuth, and User-Managed Access, fundamental elements of privacy and security on the internet. But have you ever wondered how they came to be? A lot of work on these protocols went on (and goes on) behind the scenes at the Internet Identity Workshop (IIW), a bi-annual gathering of identity experts where we work on improving the identity systems that make the web run. It’s a great event that’s flown under the radar, so I’m excited to share a new documentary on IIW, “Not Just Who They Say We Are: Claiming our identity on the Internet”. This short film shines a light on the stealth community of “Identerati” at IIW that are defining and refining digital identity.
NO ONE PERSON, COMPANY, ORGANIZATION OR GOVERNMENT RUNS THE INTERNET.
The Internet itself is a globally distributed computer network comprised of many volantarily interconnected autonomous networks. Similarly, its overnance is conducte by a decentralized and international multi-stakeholder network of interconnected autonomous groups drawing from civil society, the private sector, governments, the academic and research communities, and national and international organizations. They work cooperatively from their respective roles to create shared policies and standards that mantian the Internet’s global interoperability for the public good.
Decentralized Identity Stack
- Identity Standards From: Hyperledger Type: Wiki entry Date: 2019-05-20
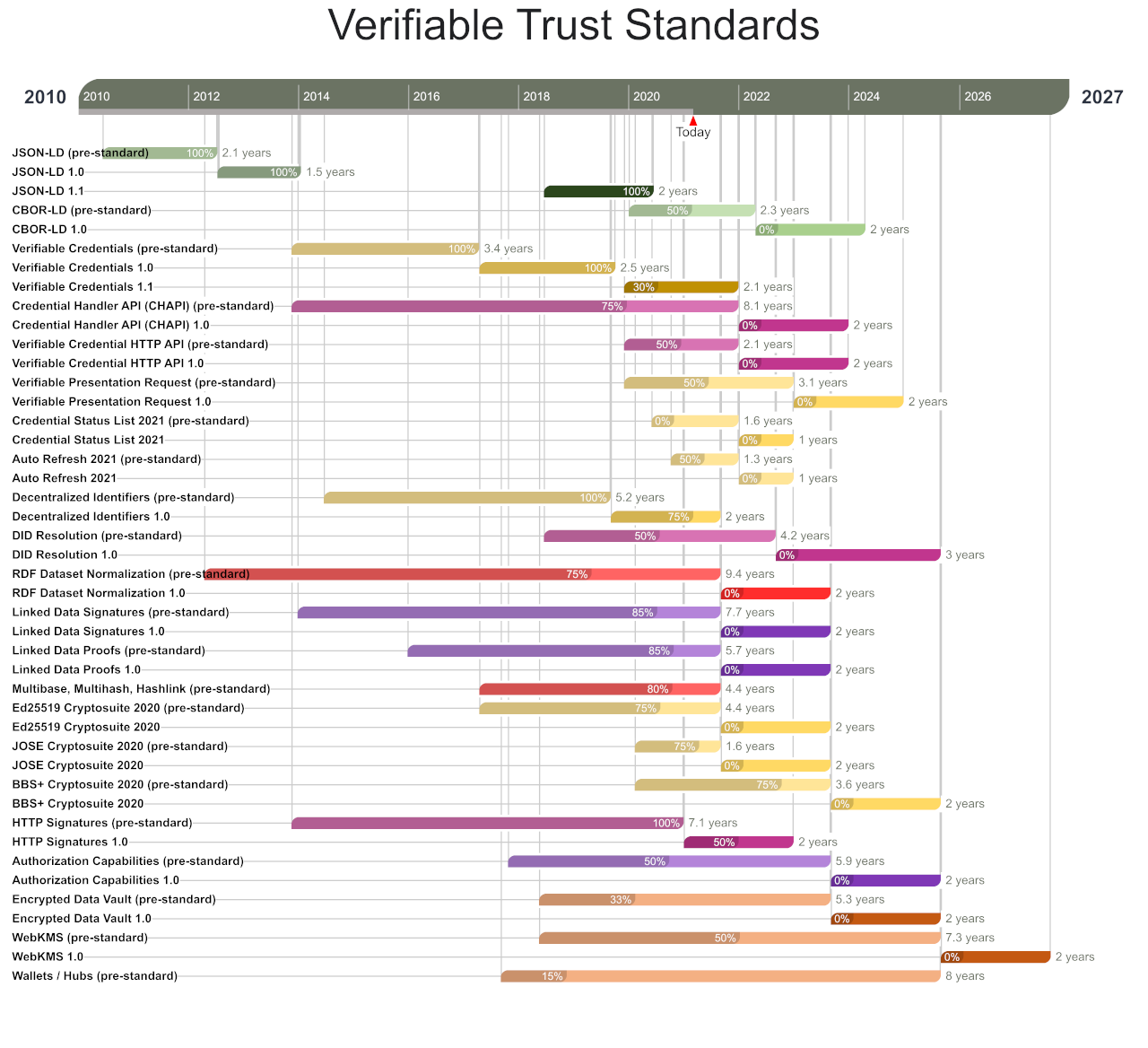
- Roadmap: Verifiable Trust Standards From: CCG Mailing List By: Manu Sporny Type: Discussion Date: 2021-03-03
- Linked Data Security From: CCG Mailing List By: Manu Sporny Type: Discussion Date: 2021-02-29
- A Taxonomic Approach to Understanding Emerging Blockchain Identity Management Systems (NIST CYBERSECURITY WHITE PAPER) From: arxiv Type: Paper Date: 2020-01-14
- Building Blocks for a New Architecture By: Tim Bouma Type: Post Date: 2019-09-23
- The Self-Sovereign Identity Stack From: DIF By: Oliver Terbu Type: Post Date: 2019-01-27
- Overview of Decentralized Identity Standards From: DIF By: Nader Helmy Type: Post Date: 2020-03-02
- The Story of Open SSI Standards From: SSIMeetup.org By: Drummond Reed Related: Evernym Type: Presentation Date: 2018-04-27

- SSI Architectural Stack and Community Efforts Overview From: DIF Type: Infographic Date: 2020-09-23
- Distributed ID Learning Path By: Kristina Yasuda Related: VC spec map Type: Post Date: 2020-12-09
- Recommendations for Decentralized Key Management Systems From: WebOfTrustInfo Type: Paper Date: 2017-09-15 Event: RWoT
- DKMS - An Essential Missing Piece of the SSI Puzzle From: SSIMeetup.org By: Drummond Reed Type: Presentation Date: 2018-06-28

- Verifiable Credentials Flavors Explained From: LPFH By: Kaliya IdentityWoman, Lucy Yang Type: Paper Date: 2021-02-11
We hope to accumulate links here that talk to all Identity Standards work. Short updates form this will be used in the paper. Some are already input into the paper and need work polishing up.
Green - General data format standards
Yellow - Vocabulary standards (I the mislabeled VC work)
Magenta - Protocol standards (I mislabeled DID Resolution)
Red - Low-level cryptographic primitives
Purple - General crypto packaging/protocol standards
Orange - Application layer standards
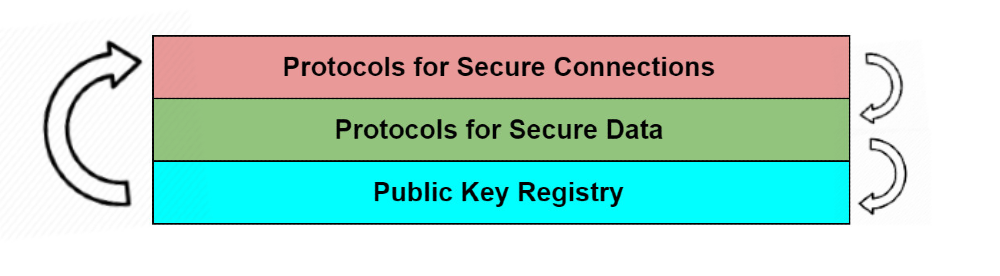
The attached slide deck provides a basic overview (with examples) of Linked Data Security as well as the specifications in that orbit. The W3C CCG is actively developing a number of these specifications.
Identity management systems (IDMSs) are widely used to provision user identities while managing authentication, authorization, and data sharing both within organizations as well as on the Internet more broadly. Traditional identity systems typically suffer from single points of failure, lack of interoperability, and privacy issues such as encouraging mass data collection and user tracking. Blockchain technology has the potential to support novel data ownership and governance models with built-in control and consent mechanisms, which may benefit both users and businesses by alleviating these concerns; as a result, blockchain-based IDMSs are beginning to proliferate. This work categorizes these systems into a taxonomy based on differences in architecture, governance models, and other salient features. We provide context for the taxonomy by describing related terms, emerging standards, and use cases, while highlighting relevant security and privacy considerations. JULY 9, 2019
First, you will see the Issuer, Holder and Verifier. This is the archetypal pattern of the decentralized architecture. An issuer issues something to a holder, who then presents it to a verifier, who make a decision. A simple example: government(issuer) issues you a passport (holder), which you present to a border control officer (verifier) who lets you through the gate. When you look at all the use cases (described above), they all fall into this pattern. https://i.imgur.com/qGXEnW1.png
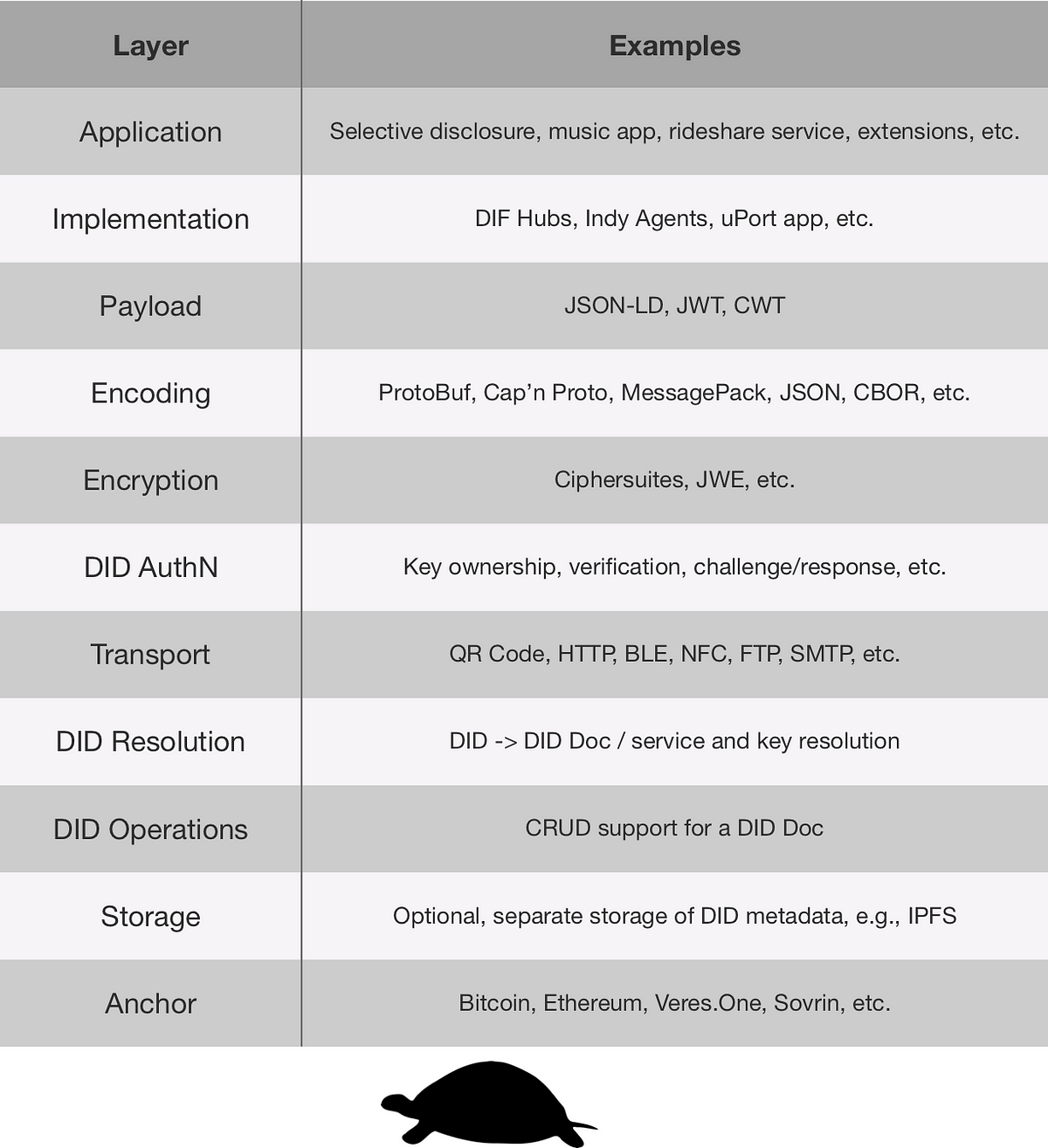
Layer Examples Application Selective Disclosure, music app, rideshare service, extensions, etc. Implementation DIF Hubs, Indy Agents, uPort app, etc. Payload JSON-LD, JWT, CWT Encoding ProtoBuf, Cap'n Proto, MessagePack, JSON, CBOR, etc. Encryption Ciphersuite, JWE, etc. DID AuthN Key ownership, verification, challenge/response, etc. Transport QR Code, HTTP, BLE, NFC, FTP, SMTP, etc. DID Resolution DID-DID Doc / service and key resolution DID Operations CRUD support for a DID Doc Storage Optional, separate storage of DID metadata Anchor Bitcoin, Ethereum, Veres One, Sovrin, etc.
we can think of each specification as addressing one or more of the SSI “building blocks” that we described above. In some cases a standard may be a bridge between layers, enabling a closer link between connections, data, and keys, making the ecosystem more secure as a whole. What you will find below is a list of all relevant standards, links to every specification, the organizations they belong to, their relationship to the ecosystem, and their relative maturity as internet technologies.
Drummond Reed, Chief Trust Officer at Evernym and Sovrin Foundation Trustee, features in our first Webinar “The Story of SSI Open Standards” by giving us the background on the foundation of Self Sovereign Identity. Drummond explains the technical and development aspects of DIDs, DKMS, DID Auth and Verifiable Credentials that will make Self Sovereign Identity possible.
While a more thorough (and competitive) separation of concerns might slice today’s and tomorrow’s identity systems into more modular and interchangeable parts at many more layers, the diagram used here organizes the space into just three broad divisions, which map roughly to the bottom three in the mapping dominant in the Aries & ToIP communities. For a more detailed and complex mapping, see the forthcoming map by the DIF interoperability working group.
There is a lot of information about decentralized IDs on the web. I struggled too. (I still do that lol)
There are many standards for decentralized identities, and they are interdependent and interrelated, as you can see from the diagram below.
A decentralized key management system (DKMS) aims to solve how consumers can manage their own keys and certificates without relying on a third-party provider having access or controls over the keys.. This method helps to ensure that no third-party can compromise the integrity and security of the system as a whole. Entities can use the system to safely authenticate each other and validate keys and certificates. Centralized key management systems (CKMS) manage key and certificate creation, signing, and validity. Specific problems arise when these authorities become unavailable, or the data they control becomes corrupted or known. Central authorities often become choice targets for attackers. This document proposes to meet these requirements with a decentralized blockchain ledger for providing an oracle of trust and leave control over all keys with end users. The use of a blockchain permits globally readable identifiers and public data to be shared in a secure manner that is not vulnerable to the man-in-the-middle attack or system wide compromise and permits consumers to be self-sovereign. This leaves consumers with the task of key management and protection. This document covers various ideas for how users may create, recover, backup, and revoke keys and provides recommended suggestions.
DKMS inverts a core assumption of conventional PKI (public key infrastructure) architecture, namely that public key certificates will be issued by centralized or federated certificate authorities (CAs). With DKMS, the initial “root of trust” for all participants is any blockchain or distributed ledger that supports DIDs. This webinar will explain why we need DKMS, what a DKMS-compatible identity wallet looks like, how DKMS can solve some longstanding problems in wallet backup and recovery, and where DKMS is headed for standardization.
Below are the three primary flavors of VCs discussed in this paper. All have more than one critical implementation in various stages of production. There are advocated variations of these types, but they are less common.
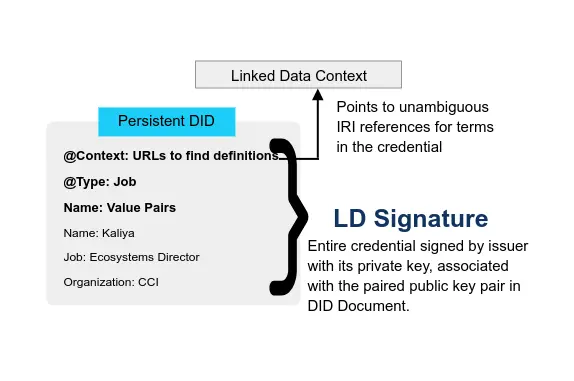
* JSON-LD family with LD Signatures or with BBS+ Signatures that enable Zero Knowledge Proofs (ZKP or ZKPs)
* JSON with JSON Web Signatures, precisely in the form of a JSON Web Token (JWT)
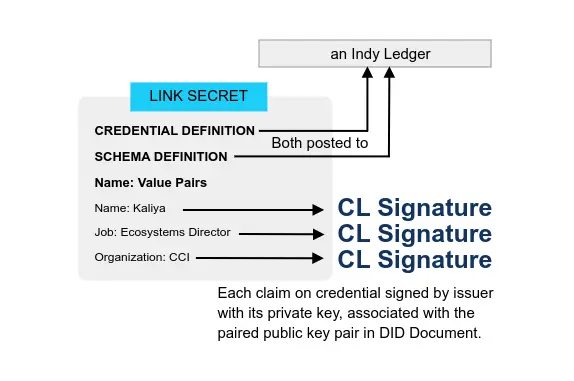
* ZKP with Camenisch-Lysyanskaya Signatures (ZKP-CL)