Verifiable Credentials - Literature, Comparisons, Explainer (W3C)
About
- Verifiable Credentials - Wikipedia From: Wikipedia Type: Wiki entry Date: 2023-04-25

- Identity, Unlocked... Explained: Season 2, Ep. 2 From: Auth0 By: Vittorio Bertocci, Filip Skokan Type: Post Date: 2021-03-12
- IIW26 Primer On DIDs and VCs From: Digital Bazaar By: Manu Sporny Type: Presentation Date: 2018-03-05 Event: IIW26, IIW

- A Gentle Introduction to Verifiable Credentials From: Evernym By: Daniel Hardman Type: Post Date: 2019-10-24
- A Verifiable Credentials Primer From: WebOfTrustInfo Type: Paper Date: 2018-07-17 Event: RWoT
- Verifiable Credentials 101 for SSI From: SSIMeetup By: Tyler Ruff Type: Presentation Date: 2018-09-12
- Verifiable Credentials: What They Are, Why They Matter From: Hackernoon Type: Post Date: 2020-10-02
- Understand Verifiable Cresidentials in 10 Minutes From: Arcblock Type: Post Date: 2020-04-15
- What are Verifiable Credentials From: Affinidi Type: Page Date: 2022-11-17
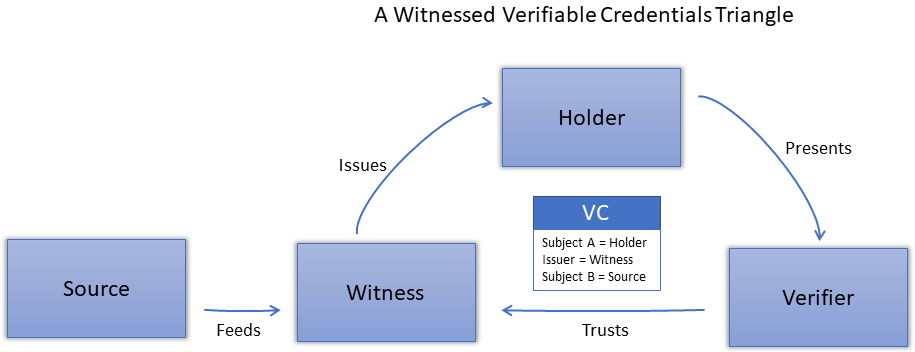
- The Role of Witness Organizations in Verifiable Credentials By: Michael Ruminer Type: Post Date: 2021-03-09 Location:
- An introductory dive into VCs (verifiable credentials) From: HackerNoon Type: Post Date: 2021-04-28
- How Does a Verifier Know the Credential is Yours? From: Evernym By: Brent Zundel Type: Post Date: 2021-08-10

- Introduction to Verifiable Credentials From: Ubisecure By: Petteri Stenius Type: Page Date: 2021-08-04
- 8 Reasons to use Verifiable Credentials From: Affinidi Type: Page Date: 2021-09-08
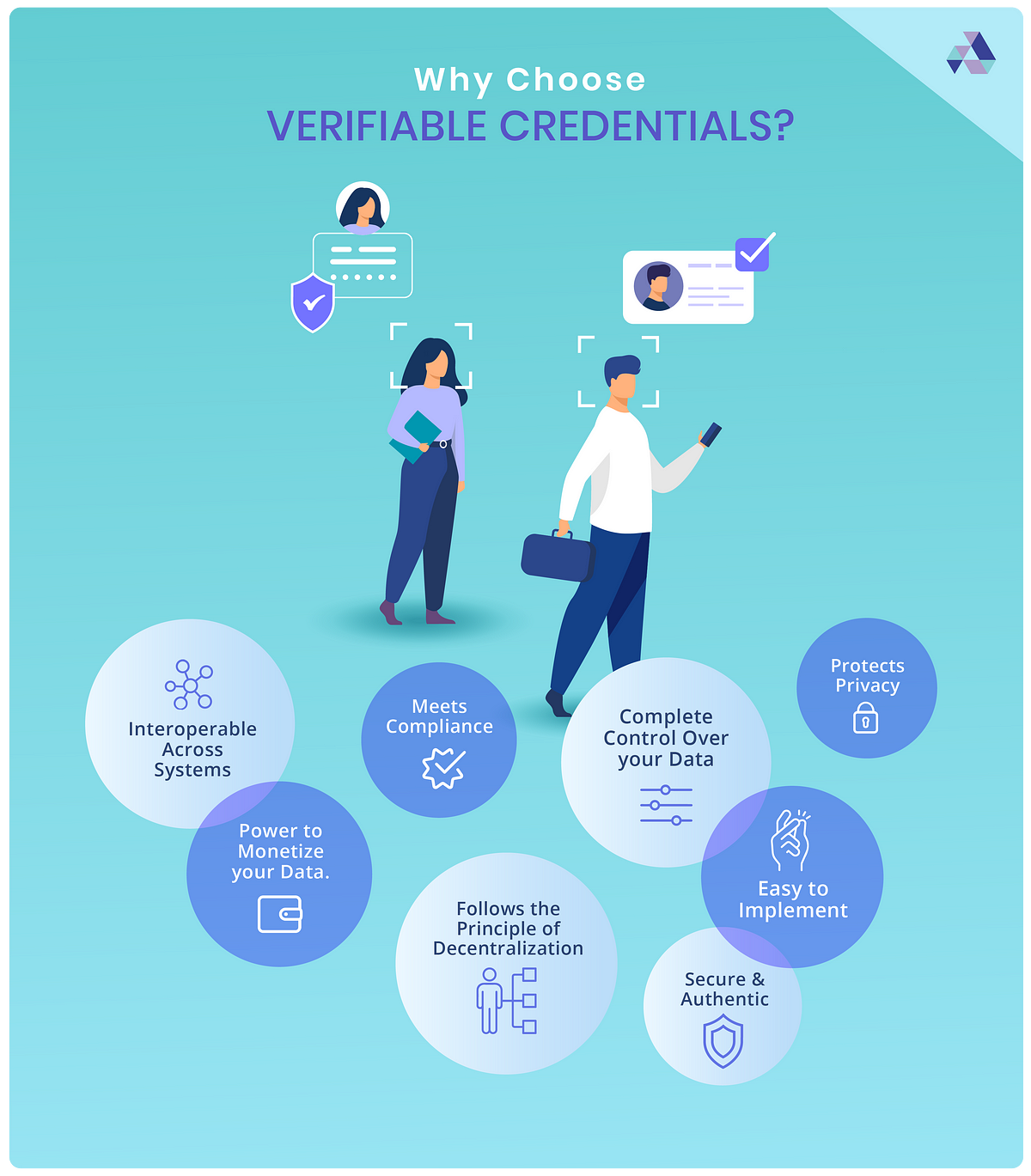
- Verifiable credentials are key to the future of online privacy From: HelpNetSecurity Type: Post Date: 2021-07-26
- All the data is decentralized, meaning there’s no need for a database of student records that could be jeopardized. Alice’s data lives with her.
- The employer doesn’t need to keep a copy of Alice’s transcript to verify her education.
- The college doesn’t play intermediary and doesn’t have access to the list of organizations Alice shares her data with. Other parties have no way of correlating this data as each exchange is private and unique.
- If desired, Alice could pick and choose what she wants to share. She could prove her degree without sharing her date of graduation or GPA, for example. - Self Attested vs Chain of Custody - assurance levels in data provenance in VCs From: IDCommons By: Stew Whitman, Alka Lachhwani Type: Session notes Date: 2021-05-06 Event: IIW
- How a combination of Federated identity and Verifiable Credentials can help with Customer onboarding From: BLOCK6 By: Pranav Kirtani Type: Post Date: 2022-07-27
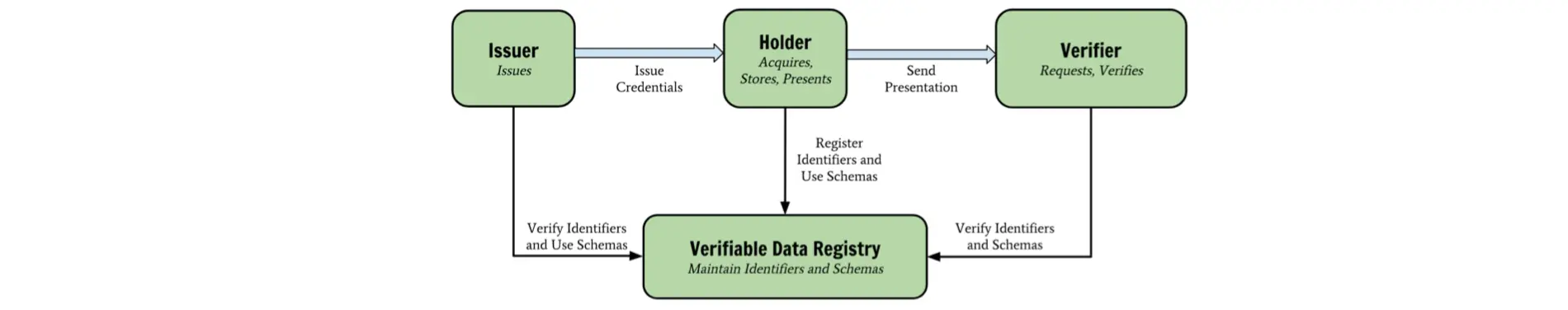
Verifiable credentials (VCs) are the electronic equivalent of the physical credentials that we all possess today, such as: plastic cards, passports, driving licences, qualifications and awards, etc. The data model for verifiable credentials is a World Wide Web Consortium Recommendation, “Verifiable Credentials Data Model 1.0 - Expressing verifiable information on the Web” published 19 November 2019.
a conversation about a few three-letter extensions to OAuth (which, incidentally, would also fit well in a pirate incantation!): PAR, RAR, and JAR. Filip is a Senior Engineer II at Auth0, the author of a popular book on open source identification, and a contributor to both the IETF and the OpenID Foundation.
$5
A new type of globally resolvable, cryptographically-verifiable identifier, registered directly on a distributed ledger (aka Blockchain). Portable identifiers for any person, organization, or thing that does not depend on a centralized authority, are protected by cryptography, and enable privacy and data portability.
But while digital records are nothing new, today’s credentials come with certain ‘cryptographic superpowers’ that make them tamperproof, secure, and verifiable. Whereas a simple digital copy of a car title can easily be edited, a verifiable digital credential is one that has been issued by a trusted authority for, and only for, its holder.
NOTE: “Verifiable Claims” are now known as “Verifiable Credentials”. The W3C Verifiable Claims Working Group’s experience with using the term “Verifiable Claims” demonstrated that it led to confusion in the marketplace. The group has since found consensus in shifting to use the term “Verifiable Credentials”, which contain “Claims”.
Tyler Ruff, product manager at Evernym, will be our next guest to walk us through Verifiable Credentials in the context of Self-Sovereign Identity. He will cover how they are created, issued and shared, as well as cover some common technical questions.
From permanent resident cards to anonymous payments to automatic notarization, verifiable credentials and DIDs are a technology whose time has arrived. Use cases are currently being piloted; many will surface in coming months and years. Security on the internet as we know it may be broken, but it is not beyond saving. A touch of the cryptographic wand, and we’ll be able to repair trust once more.
This article is a soft introduction into Verifiable Credentials and the potential use cases for organizations, businesses and government institutions and creating new levels of trust for individuals and the services/institutions they use.
At the most basic level, verifiable credentials, or VC in short, are tamper-proof credentials that can be verified cryptographically.
The basis is that not every source of a verifiable credential has an interest in issuing verifiable credentials and that it is not only logical but beneficial to the ecosystem of trust that witness organizations will issue on behalf of these sources.
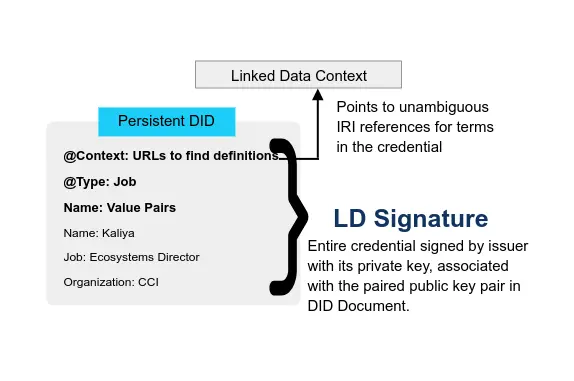
Verifiable Credentials heavily utilize Decentralized Identifiers to identify people, organizations, and things and to achieve a number of security and privacy-protecting guarantees. They are issued and cryptographically signed documents, intended to be understood by computers rather than people.
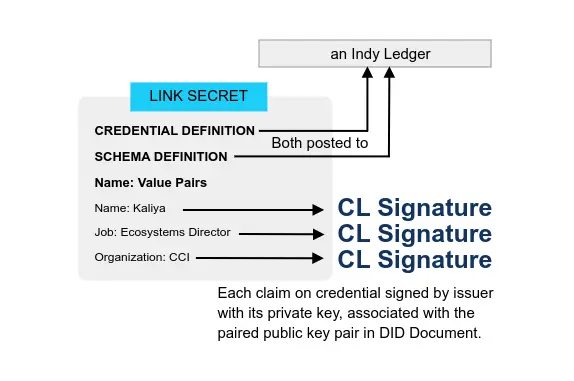
A link secret is a large random number, wrapped in a way that allows the holder to prove that they know the secret.
The Verifiable Credentials specification is quite new, and many pieces that are required to create interoperable solutions are still incomplete or missing at time of writing. However, there is significant momentum around verifiable credentials (VCs). This is partly attributed to VCs being part of the solution for blockchain-based decentralised identity.
VCs are interoperable across many systems and can be used in almost every possible scenario.
There are two important factors in establishing “truth” or the trustworthiness of the information. Attributional and Reputational. You need to have both to have trust.
Digital needs higher level of attestation because it is easier to forge and easier to propagate that forgery.
Before we dive into how Federated systems like OIDC and SAML along with Verifiable Credentials (VC) can help improve customer onboarding to your application, let us first understand what are the current methods being used for onboarding.
Comparisons
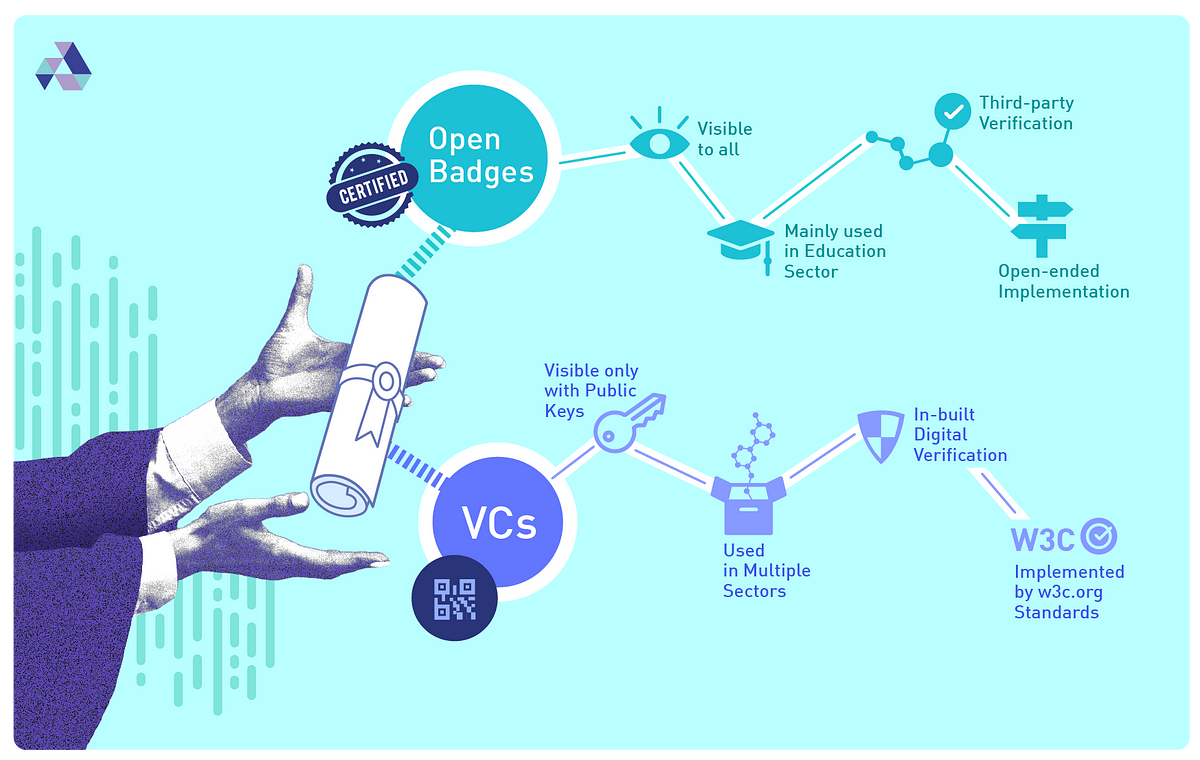
- Compare and Contrast: OpenBadges vs Verifiable Credentials From: Affinidi Related: Open Badges Type: Page Date: 2022-11-17
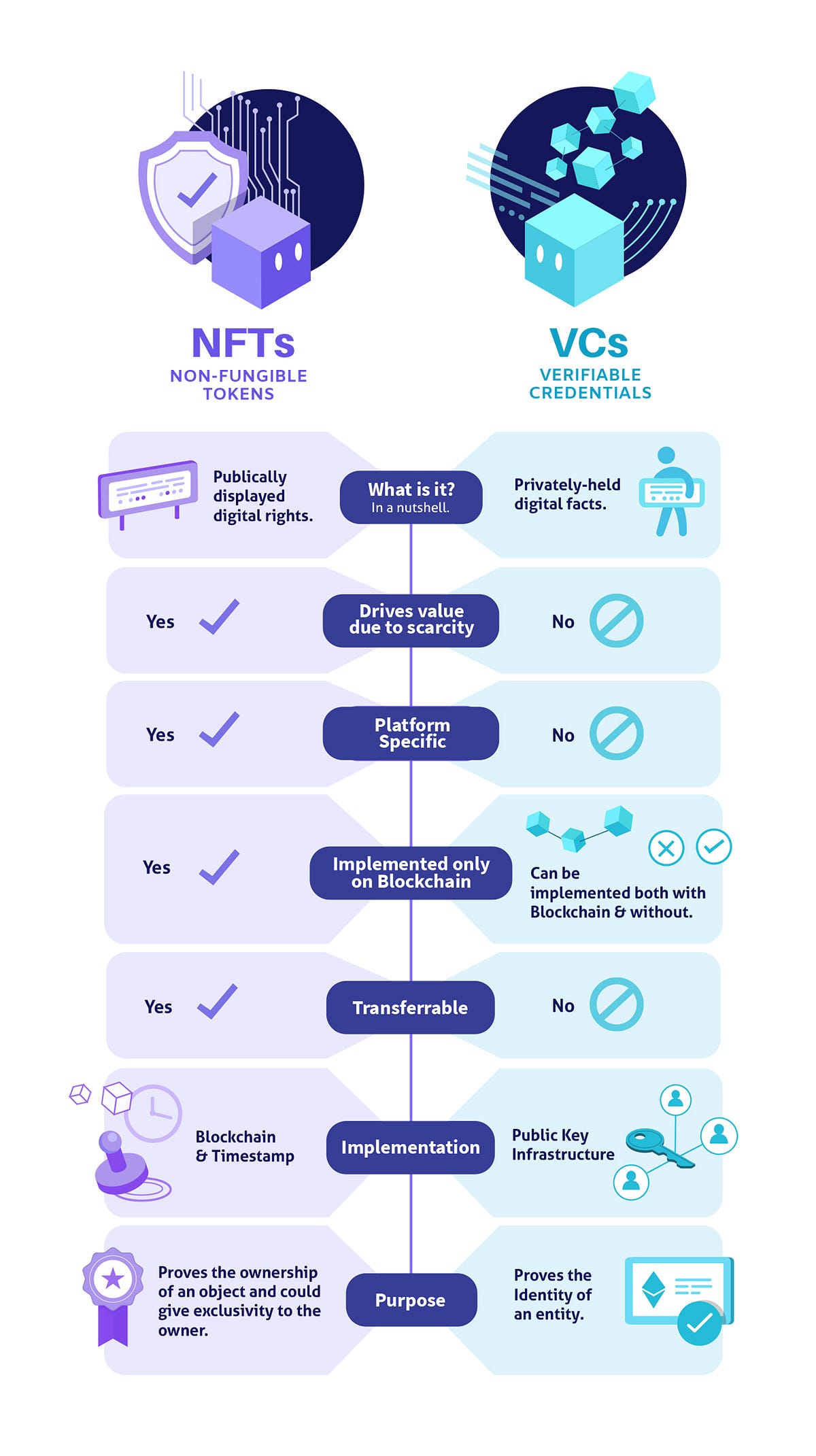
- Non-Fungible Tokens (NFTs) vs Verifiable Credentials (VCs) From: Affinidi Type: Page Date: 2022-11-17
- ERC-721 Non-Fungible Token Standard on Ethereum vs. VCs on Hyperledger Indy From: CCG Mailing List By: Michael Herman Type: Discussion Date: 2021-02-11
- Compare and Contrast — IRMA vs Verifiable Credentials From: Affinidi Type: Page Date: 2022-11-17
- Could an NFT be a VC? From: IDCommons By: Grace Rachmany Type: Session notes Date: 2021-05-06 Event: IIW
- How does VC Functional Stack compare to #ToIP Stack? By: Timothy Ruff Type: Thread Date: 2020-09-03
- ToIP Layers 2 & 3 compare to Functional Layer 2
2. ToIP Layer 4 compares to Functional Layers 3 & 4 (horizontal layer for VC Management, vertical layer for Applications)
3. Functional stack doesn’t require #blockchain
4. Functional Stack doesn’t detail steps for trust or verification; ToIP Stack doesn’t separate management or storage
5. Functional Stack clarifies functions, roles, and potential business models; ToIP stack clarifies trust & security They are complementary, not contradictory. 
- What are VCs similar to? From: CCG Mailing List By: Michael Herman Type: Discussion Date: 2021-08-23
- Hygiene for a computing pandemic From: fossandcrafts Type: Post Date: 2021-01-03 Tech: Object Capabilities
- Re: The dangers of using VCs as permission tokens (was: PROPOSALs for VC HTTP API call on 2021-06-22) By: Kyle Den Hartog, Manu Sporny Type: Post Date: 2021-06-24
- Comparing VCs to ZCAP-LD By: Kyle Den Hartog Type: Post Date: 2021-09-25 Tech: Object Capabilities
- Re: VCs - zCaps / OCap a Discussion From: CCG Mailing List By: Dave Longley Type: Discussion Date: 2020-12-05 Tech: Object Capabilities
As we move towards a world of digital identity, many ways of sharing and verifying Personally Identifiable Information are emerging. Two such modes that we’ll talk about today are Open Badges and Verifiable Credentials.
A common thread that connects both NFTs and VCs is that they leverage the potential benefits of the digital world to give users more security, flexibility, and freedom to monetize.
When are Hyperledger Indy/Sovrin VCs better than Ethereum smart contracts for NFEs/NFTs (non-fungible entities/tokens)?
It seems obvious but I don’t have a detailed/worked out answer. One project I’m associated with wants to use the ERC-721 Non-Fungible Token Standard on Ethereum but I believe VCs are a better route to take. Part of the desire to stay on Ethereum is there is quite a vibrant NFT community on Ethereum and lots of different EC-721 tokens.
IRMA [is] based on the Idemix technology. Idemix is a public-private key pair where the private key is used by the issuer to sign a credential and the public key is used by the verifier to establish that the credential is signed by the issuer and hence is authentic. […] Verifiable credentials, or VC in short, are tamper-evident credentials that can be verified cryptographically.
Case discussed: A group of villages in Africa using a cryptocurrency platform for alternative currencies. Different organizations issue the coins under different circumstances. When you accept a currency, you want to know who is the issuer. The Red Cross might be more or less trusted than the local leader or agricultural cooperative as the issuer of a currency that is supposedly equivalent to a shilling.
What types of tech could be used for this?
- Multiple currencies on the blockchains
- Certifications in the form of some kind of NFT issued by the issuer.
- Limited supply tokens or NFTs that are “expired” when you use them
- Open Credential Publisher framework was suggested
- VCs are generally authorizations associated with a person, so maybe a person could have the VC and show their credit rating in some way while they are making a transaction
- Similarly maybe the VC belongs to the organization that is issuing the coin, proving its reputation over time.
The chip in your e-passport is the analogy I’ve been most successful with
An issuer gives it to you.
You carry it around and show to whom you choose
The verifier can check its integrity without contacting the issuer
“A VC is like the chip in your passport - bit for any document type”
So far the best analogy I’ve found. Policy makers say “ah, I see”
This episode of FOSS and Crafts features Christopher Lemmer Webber discussing the object capability security approach. Its a generalization not specific to VCs, continuing from the conversation on the CCG mailinglist, Hygiene for a computing pandemic: separation of VCs and ocaps/zcaps, we shared last month.
Agreed, when it comes to the number of checks that occur it’s much greater
because of the delegation. With that in mind, looking at the semantics only
of the system VCs in my opinion weren’t optimally designed for permission
tokens. This difference between the two requires that an implementation
that wants to support both claims tokens and permissions tokens has to
grapple with the different mental model that arise when trying to stuff
these things together. This introduces additional complexity. Additionally
it leads to weird statements that are being made where it’s difficult to
tell if the VC is behaving like a claims token or a permissions token.
Yes, exactly this. Exactly what Kyle states above is the reason why it’s so complicated (and thus dangerous) to use VCs as permissions tokens.
This is one of the primary reasons that we separated out the Authorization Capabilities work from the Verifiable Credentials work. Things get really complicated when you start mixing authz/authn/claims/permissions into a Verifiable Credential. Just because you can do it doesn’t mean you should
Why make the investment then to put the time and effort into ZCAPs when we’ve already got VCs? Simply put because security is hard and trying to push square pegs into round holes often times leads to bugs which are elevated to mission critical authentication/authorization bypass vulnerabilities. By designing around a fit for purpose data model with a well defined problem being solved it allows for us to be much more precise about where we believe extensibility is important versus where normative statements should be made to simplify the processing of the data models. By extension this leads to a simpler security model and likely a much more robust design with fewer vulnerabilities.
TL; DR: My current view is that the main confusion here may be over the difference between VCs and LD Proofs, not VCs and ZCAPs. VCs are not a generalized container for attaching a cryptographic proof to a document. That’s what LD proofs (or JOSE style proofs) are for. VCs use LD proofs (or JOSE style proofs) to attach an assertion proof to a document that specifically models statements made by an issuer about some subject, which is therefore inherently about the identity of that subject
Implementations
- List of Implementations for the Verifiable Credentials Data Model From: VCWG Type: Page Date: 2022-06-03
- Go
- Credential Manifest Builders (DI & JWT)
- Hyperledger Aries Framework Go (DI & JWT)
- Java
- Verifiable Credentials Java (DI & JWT)
- JavaScript/TypeScript
- Kotlin
- Python
- Rust
- DIDKit (DI & JWT)
- Swift
- SolidVC : a decentralized framework for Verifiable Credentials on the web From: DSpace@MIT Type: Paper Date: 2019

- Blockstack and Verifiable Credentials - Paris P2P Festival From: Paris P2P Type: Presentation Date: 2020-01-10 Event: Paris P2P Festival
- Verifiable credentials and libp2p From: LibP2P Type: Discussion Date: 2019-07-09

- Verifiable Claim Protocol From: Ontology Type: Specification Date: 2017-03-20
- Crossword wins NGI Atlantic funds for Verifiable Credentials project From: Crossword Related: Cybersecurity NGI Type: Post Date: 2022-08-04

- Identity.com Verifiable Credential Library From: Identity.com Type: Code Date: 2023-02-13
SolidVC is a decentralized Verifiable Credentials platform built with the open protocols of the Web. It is implemented on top of Solid, a Web framework developed at MIT in 2016 that allows decentralized applications to interact with personal user data to provide services in an access controlled environment.
• Keep auth and smart contracts on-chain
• Keep encrypted data off-chain
> • Wrap everything in an easy JavaScript API
Hi - we’re looking into libp2p as a network stack for our application and exploring how we could integrate verifiable credentials (https://w3c.github.io/vc-data-model/ 2) infrastructure. A basic use case is that of a node being challenged to provide some specific credential to join the network. The bootstrap node handling the incoming connection should verify the credential with the issuer and complete the connection/bootstrap or terminate it.
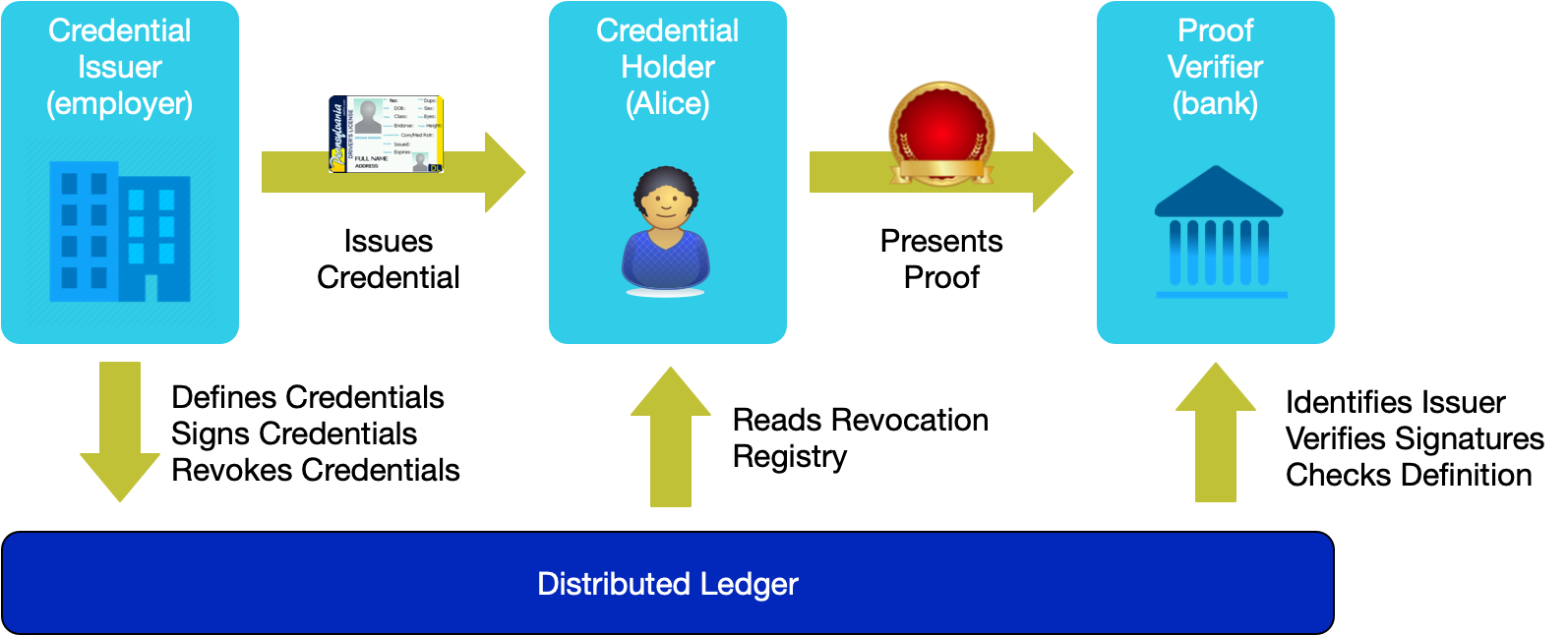
The entire workflow of the verifiable claim is shown in the figure below. It contains three major parts:
Request claim;
Issue claim;
Verify claim.
European Commission’s Next Generation Internet (NGI) initiative to lead a project to test the OpenID Foundation’s protocols for transferring verifiable credentials. Crossword’s partners in this project are Spruce Inc from the USA and Fraunhofer from Germany
This Javascript Library provides functionality around Verifiable Credentials (VC), a W3C standard. Enables Validators to issue, Credential Wallets to verify, filter and Requesters to verify credentials.
Literature
- VC Spec Enhancement Proposal By: Samuel Smith Type: Paper Date: 2022-04-04
- Verifiable Credential Exchange By: Phil Windley Type: Post Date: 2018-12-10
- Full-text Search for Verifiable Credential Metadata on Distributed Ledgers From: Service-centric Networking, Telekom Innovation Laboratories, Technische Universiät Berlin By: Zoltán András Lux, Felix Beierle, Sebastian Zickau, Sebastian Göndör Type: Paper Date: 2019-09-06
- Enabling Decentralised Identifiers and Verifiable Credentials for Constrained IoT Devices using OAuth-based Delegation From: NDSS Symposium Type: Post Date: 2020-06-08
- Distributed-Ledger-based Authentication with Decentralized Identifiers and Verifiable Credentials From: Service-centric Networking, Technische Universitat Berlin, Telekom Innovation Laboratories, Deutsche Telekom By: Zoltán András Lux, Dirk Thatmann, Sebastian Zickau, Felix Beierle Type: Paper Date: 2020-06-06
- Addition of Proof Request/Response to a formal Verifiable Credentials specification From: WebofTrustInfo Type: Paper Date: 2019-08-26 Event: RWoT
- Verifiable Credentials (DID Credential Flows) : Technical Overview By: Tsuyoshi Matsuzaki Type: Post Date: 2020-06-25
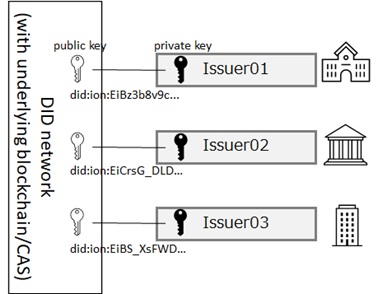
the VC standard appears to be an adoption vector for Linked Data, not the other way around. My overriding interest is that the concept of a VC as a securely attributable statement is a very powerful and attractive one and therefore should be widely adopted. We should therefore be picking the best technologies that best support broad VC adoption, not the other way around.
Multi-source identity (MSI) depends on issuing, exchanging, and verifying digital credentials. The specification for verifiable credentials is being formulated by the World Wide Web Consortium’s Verifiable Credentials Working Group. Verifiable credentials provide a standard way to express credentials in a way that is cryptographically secure, privacy respecting, and automatically verifiable.
The proposed solution is able to find credential types based on textual input from the user by using a full-text search engine and maintaining a local copy of the ledger. Thus, we do not need to rely on information about credentials coming from a very large candidate pool of third parties we would need to trust, such as the website of a company displaying its own identifier and a list of issued credentials. We have also proven the feasiblity of the concept by implementing and evaluating a prototype of the full-text credential metadata search service.
Abstract—Decentralised identifiers (DIDs) and verifiable credentials (VCs) are upcoming standards for self-sovereign privacypreserving identifiers and authorisation, respectively. This focus on privacy can help improve many services and open up new business models, but using DIDs and VCs directly on constrained IoT devices can be problematic due to the management and resource overhead. This paper presents an OAuth-based method to delegate the processing and access policy management to the Authorisation Server thus allowing also systems with constrained IoT devices to benefit from DIDs and VCs.
Authentication with username and password is becoming an inconvenient process for the user. End users typically have little control over their personal privacy, and data breaches effecting millions of users have already happened several times. We have implemented a proof of concept decentralized OpenID Connect Provider by marrying it with Self-Sovereign Identity, which gives users the freedom to choose from a very large pool of identity providers instead of just a select few corporations, thus enabling the democratization of the highly centralized digital identity landscape. Furthermore, we propose a verifiable credential powered decentralized Public Key Infrastructure using distributed ledger technologies, which creates a straightforward and verifiable way for retrieving digital certificates.
The W3C Verifiable Credentials (hereafter VC) specification does not currently outline how credential data should be requested by a Verifier. This document outlines the approach taken at Workday and proposes it as an addition or companion to the VC spec.
At RWoT we wish to present our approach in order to get community feedback and consensus. Workday recently announced our credentialing platform and will shortly begin to issue credentials within our market verticals. We fully intend to support the community standards around credentialing and therefore wish to drive consensus in the community on a simple, standard approach for requesting and sharing VCs between a holder and verifier.
In the perspective of W3C specification, verifiable credential (VC) doesn’t rely on DID specification. (i.e, The “id” property used in VC shouldn’t be necessarily a DID.) However, in its real implementations, it might be expected that verifiable credentials will resolve DIDs with consistent decentralized manners and technologies. Then, in this post, we also assume that DID is used with verifiable credentials.
In order to explain things plainly, I’ll include not only VC flows, but also other parts of flows, such as, DID flows or OpenID compliant flows.
Use Case
- Add Your VC-EDU Use Cases From: CCG Mailing List By: Kerri Lemoie Type: Discussion Date: 2021-07-30
- W3C Verifiable Credentials Education Task Force 2022 Planning By: Kerri Lemoie Type: Post Date: 2022-01-18
- Better digital living with blockchain-backed verifiable credentials From: The Paypers Type: Post Date: 2021-08-06
- On Climate Crisis and Self-Sovereign Verifiable Career Credentials From: Velocity Network Type: Post Date: 2021-08-12
- The World of Anonymous Credentials From: Dock Type: Post Date: 2022-01-20
- 25 Use Cases for Verifiable Credentials From: LTO Network Related: Sphereon Type: Paper Date: 2021-05-11
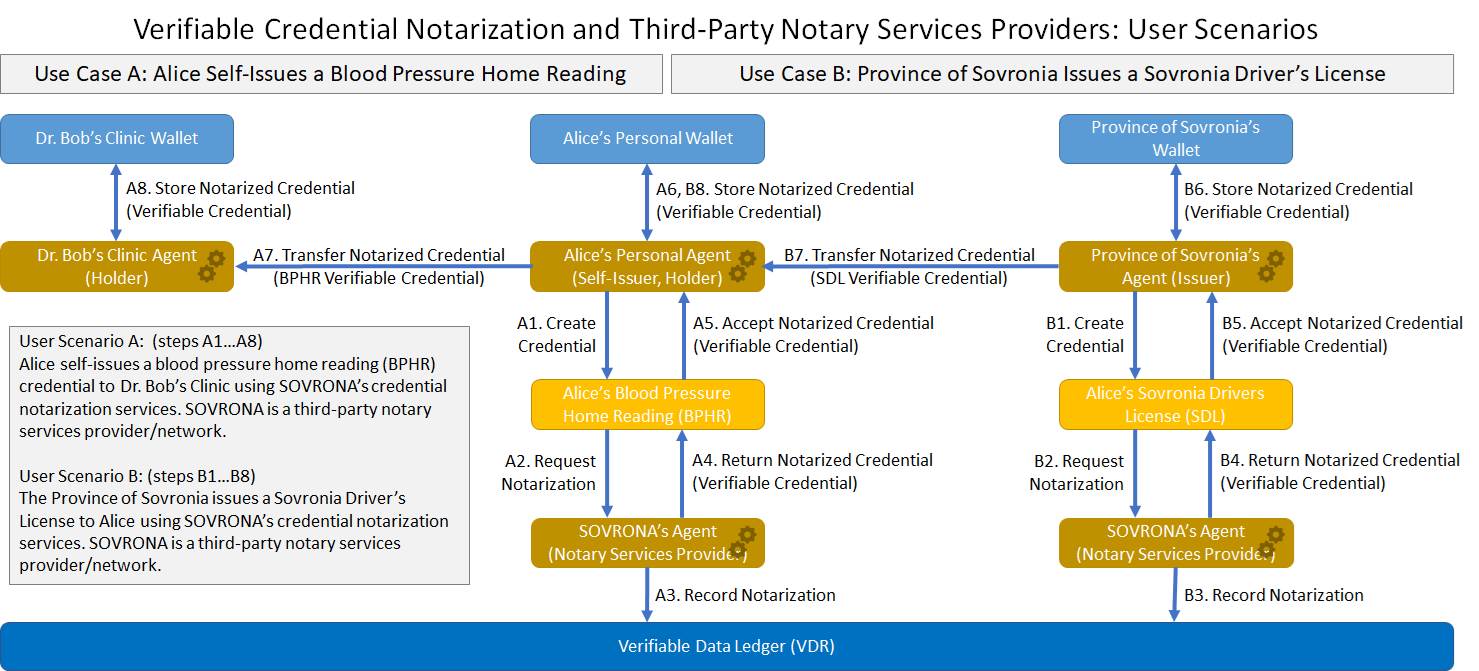
- Verifiable Credential Notarization and Third-Party Notary Services Providers: User Scenarios From: CCG Mailing List By: Michael Herman Type: User journies Date: 2021-07-15
- Verifiable Credentials for Authentic Data in the Supply Chain From: IDCommons By: Gena Morgan, Kevin Dean Related: IDCommons Type: Session notes Date: 2021-05-06 Event: IIW
- Verifiable Credentials for Assets From: IDCommons By: Mahmoud Alkhraishi Related: IDCommons Type: Session notes Date: 2021-05-07 Event: IIW
For Github users, submit your use cases as issues here: https://github.com/w3c-ccg/vc-ed-use-cases/issues
This template can help guide you: https://github.com/w3c-ccg/vc-ed-use-cases/blob/main/.github/ISSUE_TEMPLATE/use-case-template.md
We’ve been hard at work writing use cases, helping education standards organizations understand and align with VCs, and we’ve been heading towards a model recommendation doc for the community.
The NHS can now provide you with a digital verifiable credential to prove your vaccination status, securely stored in the NHS app and easily accessible, generating a QR code to prove to airlines and employers that you are fit to fly or work. But this is just the first step in the development of an enabling technology that can bring benefits to many areas of modern life.
This rich verifiable self-sovereign career identity will be the ‘great transformer’ of the global labor market. It will change the way people navigate their careers and livelihoods, and how employers make talent decisions.
A credential is called a verifiable credential when its authenticity can be cryptographically checked by anyone because the credential contains a cryptographic signature by the issuer, and the issuer’s public key is well known.
Age-related Goods or Services, Verifying Educational Qualifications, Employment Endorsements, Background Checks, Protecting your Identity Papers, Validity of Visas, Health Checks, Sharing Health Data and Medical Records, COVID Tests for Safe Travel, Generating Boarding Pass, Checking Tickets, Access to Events or Restricted Spaces, Application for Credit Cards, Checking Eligibility for Rentals, Application for Utility Connections, Access to Services, Applying and Approving Loans, Selling/Buying a Property, Computing the Insurance Premiums, Submitting and Handling of Claims, Using Death Certificates, Driving Offences, Web shop onboarding and access, Loyalty Programs, B2B Trade
User Scenario A: Alice self-issues a blood pressure home reading (BPHR) credential to Dr. Bob’s Clinic using SOVRONA’s credential notarization services. SOVRONA is a third-party notary services provider/network.
User Scenario B: The Province of Sovronia issues a Sovronia Driver’s License to Alice using SOVRONA’s credential notarization services. SOVRONA is a third-party notary services provider/network.
Using DiDs and VCs for verifiable product data in supply chains, leveraging the largest supply chain standard system in the world,
2.5 million users companies, over 6 billion product scans per day
Product data and attestations from a number of various authoritative sources
Leverage DIDs/VCs for distributed data sharing, verification
General Framework on how to think of VCs for Assets including leveraging GS1 and other vocabularies in the traceability vocab.
Requirements and Opportunities that block adoption of VCs in Supply chains