Verifiable Credentials - Working Groups, Standards and Development
Verifiable Credentials Working Group
- Verifiable Credentials Working Group From: W3C Type: Working group Established: 2017-04-14
- Verifiable Credentials Data Model v1.1 is an official W3C standard! From: VCWG By: Manu Sporny Type: Specificationification Date: 2022-03-03
- Verifiable Credentials Data Model v1.1 From: VCWG Type: Specificationification Date: 2022-03-03
- Verifiable Credentials Data Model v2.0 From: VCWG Type: Specificationification Date: 2023-05-20
- The components that constitute a verifiable credential
- Verifiable Credential Data Integrity 1.0 From: VCWG Type: Specification Date: 2023-05-15 Focus: Cryptography
- Verifiable Credentials Status List v2021 From: VCWG Type: Specification Date: 2023-04-27
- Verifiable Credentials Implementation Guidelines 1.0 From: VCWG Type: Guidance Date: 2023-02-03
- W3C Verifiable Credentials WG Test Suite From: VCWG Type: Code Date: 2021-10-31
- Verifiable Credentials Use Cases From: VCWG Type: Specification Date: 2019-09-24

- Verifiable Credentials Data Model Implementation Report 1.0 From: VCWG Type: Report Date: 2021-10-30
- The Verifiable Credential Specifications Directory From: VCWG Type: Registry Date: 2023-04-08
- ECDSA Cryptosuite v2019 From: VCWG Type: Specification Date: 2023-05-18 Focus: Cryptography
- EdDSA Cryptosuite v2022 From: VCWG Type: Specification Date: 2023-05-18 Focus: Cryptography
- BBS Cryptosuite v2023 From: VCWG Type: Specification Date: 2023-05-18 Focus: Cryptography
- JSON Web Signatures for Data Integrity Proofs From: VCWG Type: Specification Date: 2023-01-27 Focus: Cryptography
- Securing Verifiable Credentials using JSON Web Tokens From: VCWG Type: Specification Date: 2023-05-15 Focus: Cryptography
The mission of the Verifiable Credentials (formerly known as Verifiable Claims) Working Group (VCWG) is to make expressing and exchanging credentials that have been verified by a third party easier and more secure on the Web.
The Chairs of the Working Group are Kristina Yasuda and Brent Zundel. The W3C Staff Contact for the Working Group is Ivan Herman.
It’s official, the Verifiable Credentials Data Model v1.1 is a W3C standard!
Verifiable Credentials Data Model v1.1
https://www.w3.org/TR/2022/REC-vc-data-model-20220303/
This was largely a maintenance release of the specification. The list of (minor) revisions since the v1.0 release can be found here:https://www.w3.org/TR/2022/REC-vc-data-model-20220303/#revision-history
Credentials are a part of our daily lives; driver’s licenses are used to assert that we are capable of operating a motor vehicle, university degrees can be used to assert our level of education, and government-issued passports enable us to travel between countries. This specification provides a mechanism to express these sorts of credentials on the Web in a way that is cryptographically secure, privacy respecting, and machine-verifiable.
This specification describes mechanisms for ensuring the authenticity and integrity of Verifiable Credentials and similar types of constrained digital documents using cryptography, especially through the use of digital signatures and related mathematical proofs.
This specification describes a privacy-preserving, space-efficient, and high-performance mechanism for publishing status information such as suspension or revocation of Verifiable Credentials.
This guide provides some examples and resources for implementing protocols which make use of verifiable credentials, beyond those available in the core specification.
Any conforming implementation MUST pass all tests in the test suite. There are multiple test suites, each of which is detailed below. You can review the current draft implementation report.
This document does NOT attempt to define an architecture for the support of Verifiable Claims. Instead it expresses the sorts of needs that real users have that could be addressed through support for some sort of self-sovereign claim environment. It attempts to use terminology that is consistent with the other deliverables of the Verifiable Claims Working Group (you can see the relevant terms in Appendix A).
The use cases outlined here are provided in order to make progress toward possible future standardization and interoperability of both low- and high-stakes claims with the goals of storing, transmitting, and receiving digitally verifiable proof of attributes such as qualifications and achievements. The use cases in this document focus on concrete scenarios that the technology defined by the group should address.
The purpose of this document is to demonstrate that there are at least two interoperable implementations of processors that are capable of generating output that is conformant to the Verifiable Credentials Data Model.
This document serves as an unofficial directory for all known Verifiable Credential specifications whether they are released by a global standards setting organization, a community group, an open source project, or an individual.
This specification describes a Data Integrity Cryptosuite for use when generating a digital signature using the Elliptic Curve Digital Signature Algorithm (ECDSA) based on the Standards for Efficient Cryptography over prime fields using a verifiably random Elliptic Curve (secpr1).
This specification describes a Data Integrity cryptographic suite for use when creating or verifying a digital signature using the twisted Edwards Curve Digital Signature Algorithm (EdDSA) and Curve25519 (ed25519).
This specification describes the BBS+ Signature Suite created in 2023 for the Data Integrity specification. The Signature Suite utilizes BBS+ signatures to provide the capability of zero knowledge proof disclosures.
This specification describes a JSON Web Signature Suite created in 2020 for the Verifiable Credentials Data Integrity Proof specification. The Signature Suite utilizes Detached JWS signatures to provide support for a subset of the digital signature algorithms registered with IANA.
This specification defines how Verifiable Credentials can be represented as JSON Web Tokens (JWT) [RFC7519] and secured using JSON Web Signatures (JWS) [RFC7515].
Credentials Community Group
- Credentials Community Group From: W3C Related: Verifiable Credentials, Decentralized Identifiers Type: Working group Established: 2014-08-19
- W3C CCG meeting transcripts From: CCG Type: Page
- W3C CCG announcements From: CCG Type: Page Event: RWOT, IIW
- W3C CCG Work Item Process From: CCG Type: Page
- WORK ITEM: Drafts and Ideas of Educational and Occupational Verifiable Credentials - w3c-ccg/edu_occ_verifiable_credentials From: CCG Related: Global Open Badges Workgroup, Verifiable Credentials WG, Credentials Commiunity Group, Schema.org Type: Code
- WORK ITEM: Verifiable Credentials Examples From: CCG Type: Code
- Verifiable Credentials Extension Registry From: CCG Type: Report Date: 2022-11-14
- This document contains a list of all known Verifiable Credential extensions and their associated specifications. Credentials Community Group
- Ed25519Signature2018 From: CCG By: Markus Sabadello Type: Report Date: 2021-07-23 Focus: Proof Methods
- RsaSignature2018 From: CCG By: Manu Sporny, Dave Longley Type: Report Date: 2020-05-26 Focus: Proof Methods
- CredentialStatusList2017 From: CCG By: Manu Sporny, Dave Longley Type: Report Date: 2020-12-29 Focus: Status Methods
- Ecdsa Secp256k1 Signature 2019 From: CCG Type: Code Date: 2020-04-08
- Verifiable Credential JSON Schemas From: CCG Type: Code Date: 2023-05-24
- Traceability Vocabulary v0.1 From: CCG Type: Specification Date: 2023-05-23

The mission of the Credentials Community Group is to explore the creation, storage, presentation, verification, and user control of credentials. We focus on a verifiable credential (a set of claims) created by an issuer about a subject—a person, group, or thing—and seek solutions inclusive of approaches such as: self-sovereign identity; presentation of proofs by the bearer; data minimization; and centralized, federated, and decentralized registry and identity systems. Our tasks include drafting and incubating Internet specifications for further standardization and prototyping and testing reference implementations.
This repo contains the meeting archives for the W3C-CCG (Credentials Community Group), including transcripts based on the IRC logs and audio files for our regular meetings, ancillary material such as slide presentations, etc. The archives for 2014-2019 can be found here.
Announcements and events associated with the W3C Credentials CG
This lets you write your specs in markdown, or technically bikeshed – a markdown document, with special extensions understood by the bikeshed tool. The bikeshed tool is run on-commit via the spec-prod github action, generating the familiar “spec looking” ReSpec format. ReSpec is just html with a javascript ReSpec library.
Work on describing credentials is occurring within the IMS Global Open Badges Workgroup, W3C Verifiable Credentials Working Group, W3C Credentials Commiunity Group, Educational and Occupational Credentials in Schema.org Community Group, and Credential Engine/CTDL.
This effort will result in requirements, use cases, and/or draft specs to be formalized in the appropriate standards group
This GitHub Pages Website hosts example credentials, as well as documents needed to construct them. When contributing an example, you are encouraged to provide everything needed to generate an verify a credential. Do your best not to include ANY broken links or missing documentation. If possible, try to make the credential id resolvable as well.
This specification describes a standard signature suite created in 2018 for the Linked Data Signatures [LD-SIGNATURES] specification. It uses the RDF Dataset Normalization Algorithm [RDF-DATASET-NORMALIZATION] to transform the input document into its canonical form. It uses SHA-256 [RFC6234] as the message digest algorithm and Ed25519 [ED25519] as the signature algorithm.
This specification describes the RSA Signature Suite created in 2018 for the Linked Data Signatures [LD-SIGNATURES] specification. It uses the RDF Dataset CANONICALIZATION Algorithm [RDF-DATASET-CANONICALIZATION] to transform the input document into its canonical form. It uses SHA-256 [RFC6234] as the message digest algorithm and the RS256 algorithm defined in JSON Web Signatures [RFC7515] as the signature algorithm.
A simple list-based mechanism for publishing and checking the status of a credential
This specification describes the Ecdsa Secp256k1 Signature created in 2019 for the Linked Data Signatures specification
The VC_DATA_MODEL specifies the models used for Verifiable Credentials and Verifiable Presentations, and explains the relationships between three parties: issuer, holder, and verifier. A critical piece of infrastructure out of the scope of those specifications is the Credential Schema.
This specification describes a Linked Data vocabulary for asserting Verifiable Credentials related to supply chain and other traceability information, similar to what is often referred to as “provenance”, including country of origin, chemical properties, mechanical properties, and other attributes of products and materials. VCs using these terms can then be used to help determine the legitimacy of organizations participating in global trade and the status of the products and materials described therein
Claims and Credentials Working Group
- Claims and Credentials Working Group From: DIF Type: Page Date: 2020-09-18
- presentation-exchange From: DIF Type: Code Date: 2023-05-31
- presentation-request From: DIF Type: Code Date: 2020-01-08
- Credential Manifest From: DIF Type: Page Date: 2023-05-04
Join this group to contribute to the standards and technology that create, exchange, and verify claims and credentials in a decentralized identity ecosystem. For example, a cryptographically verifiable credential that proves an individual has a college degree or is of a certain age. Our members focus on specs that are vendor agnostic and based on industry standards.
Specification that codifies an inter-related pair of data formats for defining proof presentations (Presentation Definition) and subsequent proof submissions
Requirements Analysis and Protocol Design for a VC Presentation Request Format
Credential Manifests do not themselves define the contents of the output credential(s), the process the Issuer uses to evaluate the submitted inputs, or the protocol Issuers, Subjects, and their User Agents rely on to negotiate credential issuance. Instead, Credential Manifests are a data model for issuers to publish and/or send individually to would-be holders, allowing the software of the latter to understand and negotiate an issuance process.
Varieties
- Verifiable Credentials Flavors Explained From: LPFH By: Kaliya IdentityWoman, Lucy Yang Type: Paper Date: 2021-02-11
- Categorizing Verifiable Credentials - Evernym From: Evernym By: Daniel Hardman Type: Post Date: 2019-11-07
- Why the Verifiable Credentials Community Should Converge on BBS+ From: Evernym By: Brent Zundel Type: Post Date: 2021-03-24
- The original #VerifiableCredentials were PKI-based SIM cards and EMV cards. By: Steve Lockstep Type: Tweet Date: 2021-06-27

Below are the three primary flavors of VCs discussed in this paper. All have more than one critical implementation in various stages of production. There are advocated variations of these types, but they are less common.
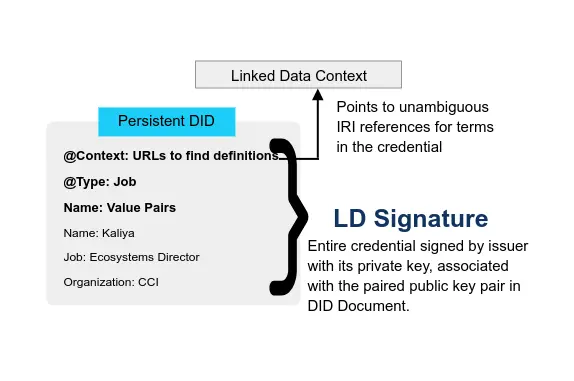
* JSON-LD family with LD Signatures or with BBS+ Signatures that enable Zero Knowledge Proofs (ZKP or ZKPs)
* JSON with JSON Web Signatures, precisely in the form of a JSON Web Token (JWT)
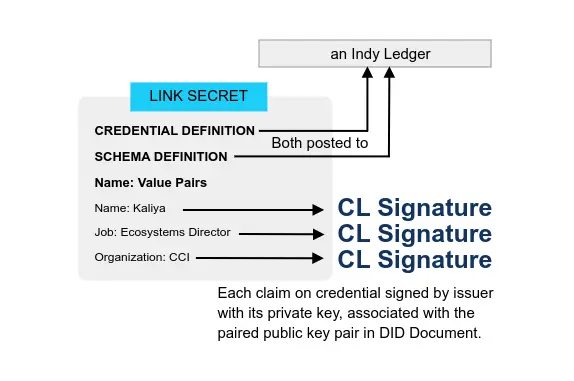
* ZKP with Camenisch-Lysyanskaya Signatures (ZKP-CL)
Not all verifiable credentials are created the same. This post examines the categories of credentials and the architectural choices driving this variation.
BBS+ LD-Proofs use JSON-LD schemas, so credentials that use them can have a rich, hierarchical set of attributes. Instead of the heavy-handed mechanism for the encoding and canonicalization of attributes values that we’d imagined for Rich Schemas, they use RDF canonicalization and a hash function. Rather than expanding the credential definition, they discarded it, taking advantage of some properties of BBS+ keys which allow for deterministic expansion.
These bind key pairs to individuals, and to signed assertions (account numbers) to deliver provenance, fidelity and proof of possession. https://constellationr.com/blog-news/not-too-much-identity-technology-and-not-too-little
$5
User Experience
- Using Paper-based Structured Credentials to Humanize Verifiable Credentials From: Trusted Digital Web Type: Video Date: 2021-11-19
- Rendering Verifiable Credentials From: WebofTrustInfo By: Manu Sporny Type: Paper Date: 2022-07-17 Event: RWoT
User Scenario: ABC Grocery wants to use the Trusted Digital Web to issue a Purchase Order for 10 cabbages from David’s Cabbages. Michael Herman
This paper explores ways in which the Verifiable Credentials data model could be extended to support visual, audio, and physical renderings for Verifiable Credentials.