Verifiable Credentials (ZKP-CL) Anoncreds
Main
Website - Specification - Specification V2
Hyperledger AnonCreds – short for “Anonymous Credentials”- is the most commonly used Verifiable Credential (VC) format in the world. Ledger agnostic and with a formal open specification, AnonCreds is a VC format that adds important privacy-protecting ZKP (zero-knowledge proof) capabilities to the core VC assurances.
-
Hyperledger launches new digital identity project, AnonCreds 2022-11-15
The technology itself is not new, as it was originally part of Hyperledger Indy, the digital identity ledger project. However, it has now been separated from Indy so that it can be used for verifiable credentials on ledgers such as Hyperledger Fabric or Ethereum-based Hyperledger Besu, or others.
-
Verifiable Credentials Flavors Explained 2021 CCI Kaliya ‘Identity Woman’ Young
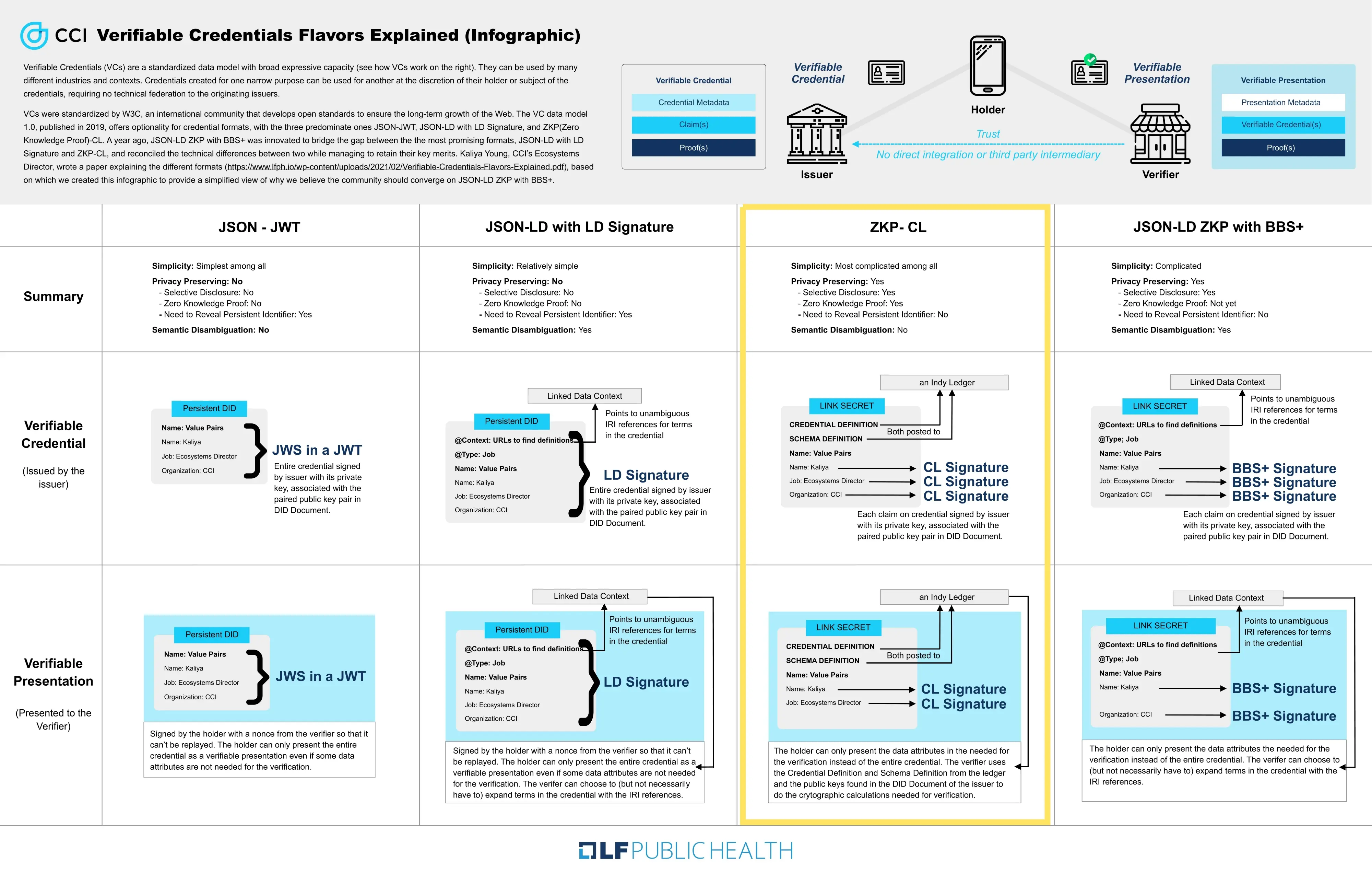
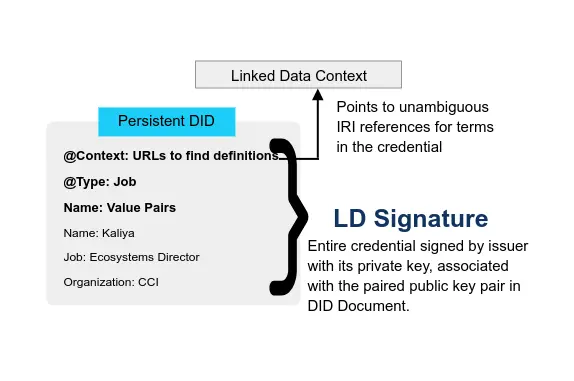
ZKP-CL: This credential format was created specifically to leverage the CL Signatures. JSON-JWT and JSON-LD Signatures each have their own way of representing the meaning of the attributes within a VC. JSON-JWT references an IANA registry and assumes a “closed world” authority model based on that authoritative registry. JSON-LD Signatures use an @context field to reference existing RDF mapping to known dictionaries and assumes an open world model where new terms and definitions can easily be introduced
- [Literature] A Signature Scheme with Efficient Protocols 2001 Jan Camenisch IBM Zurich, Anna Lysyanskaya Brown
Digital signature schemes are a fundamental cryptographic primitive, of use both in its own right, and as a building block in cryptographic protocol design. In this paper, we propose a practical and provably secure signature scheme and show protocols (1) for issuing a signature on a committed value (so the signer has no information about the signed value), and (2) for proving knowledge of a signature on a committed value. This signature scheme and corresponding protocols are a building block for the design of anonymity-enhancing cryptographic systems, such as electronic cash, group signatures, and anonymous credential systems. The security of our signature scheme and protocols relies on the Strong RSA assumption. These results are a generalization of the anonymous credential system of Camenisch and Lysyanskaya
Working Group
-
AnonCreds Specification Working Group 2022-11-02
The AnonCreds Specification Working Group operates under the Community Specification License v1.0 to create the AnonCreds Specification. Current work is focused on Version 1.0 of the specification that covers the current CL-Signatures-based implementation of AnonCreds agnostic to the underlying ledger.
- [Video] Hyperledger AnonCreds Specification Working Group 2023-06-19 Hyperledger Foundation
The big thing I want to talk about was a couple of things on revocation approaches and and go over possibilities. There, there’s a few things happening that I wanted to share. […] as I mentioned in our credits announcements, the 0.1.0 rust implementation was officially released
Development
-
Hyperledger AnonCreds Workshop: Using ZKP Verifiable Credentials Everywhere 2023-05-31 Hyperledger Foundation
AnonCreds was accepted as an Incubated project at Hyperledger in late 2022. This is the first workshop developed by this community and it is intended for anyone interested in using Zero Knowledge Proofs (ZKPs) in a wide variety of contexts.
-
anoncreds-rs 2023-06-02 Hyperledger
Rust library and reference implementation of the Anoncreds V1.0 specification.
Background
-
Wrapping Indy Credentials (AnonCreds) in W3C VCs 2021-04-12 Finema
AnonCreds are typically bound to a holder by using a link secret and not by issuing a credential to a public DID. In order to add such a credential (or a subset of attributes) to the public profile, we suggest the following mechanism which expresses the intent: I self-attest that I have this credential with the specific attribute values, if you require a proof you can ask me using the Aries present proof protocol.
-
Anonymous Credential Part 2: Selective Disclosure and CL Signature 2021-02-04 Finema
selective disclosure and an anonymous credential (Anoncred) relies on an efficient signature scheme that supports multiple messages with a single signature. One such signature scheme is known as CL signature that is named after its Jan Camenisch and Anna Lysyanskaya […] CL signature popularized Anoncreds, and it also served as a cryptographic building block in Identity Mixer (Idemix) and Hyperledger Indy projects.
-
Anonymous Credential Part 1: Brief Overview and History 2020-10-01
An anonymous credential (Anoncred), which is also known as an attribute-based credential (ABC), is a concept for a digital credential that provides a credential holder maximal privacy and an ability to selectively disclose their personal information.
-
CL Signatures for Anonymous Credentials 2019-01-14 Will Abramson
A CL Signature is a signature scheme developed by Jan Camenisch and Anna Lysyanskaya. This scheme has some properties that make it ideal for use in an anonymous credential system and is, in fact, the scheme that Sovrin, and I am sure others, currently use. In this post, I will try to synthesise my current understanding of this scheme, including a look at how Sovrin uses it in practice.
-
Attribute Based Credentials and Variable Length Data Graphs 2018-02-28
In an effort to allow JSON-LD data structures to leverage attribute based credentials and zero knowledge signature schemes, this paper outlines differences, requirements and possible options for representing JSON-LD data in attribute based credential schemes such as the one in use by the Sovrin network, implemented in the Hyperledger Indy project.
Critique
-
Being “Real” about Hyperledger Indy & Aries / Anoncreds 2022-09-10 IdentityWoman
This article surfaces a synthesis of challenges / concerns about Hyperledger Indy & Aries / Anoncreds, the most marketed Self-Sovereign Identity technical stack. It is aimed to provide both business and technical decision makers a better understanding of the real technical issues and related business risks of Hyperledger Indy & Aries / Anoncreds, which have not been shared and discussed openly or publicly as the author believes need to be.
Response
-
Hyperledger launches new digital identity project, AnonCreds 2022-11-15
The technology itself is not new, as it was originally part of Hyperledger Indy, the digital identity ledger project. However, it has now been separated from Indy so that it can be used for verifiable credentials on ledgers such as Hyperledger Fabric or Ethereum-based Hyperledger Besu, or others.
-
A response to Identity Woman’s recent blog post about Anoncreds 2022-09-08 Kyle Den Hartog
It’s only when I started to take a step back that I realized that the architecture of Indy being a private, permissioned ledger leaves it heading in the same direction as many large corporations now extinct browser and intranet projects for many of the same reasons.
-
Moving Toward Identity Technology Ready for Mass Adoption 2022-09-09 Trinsic
when we realized our customers were facing critical limitations caused by the underlying tech stack, we began developing an updated version of our platform that would reduce our dependency on these technologies and enable a better platform for our customers.
- Response to Kaliya’s “Being Real” Post
Link Secrets and Privacy-Trust Paper
- Significant section of critique discusses link secrets
- Repeats old claim they are insecure
- Cites 2019 paper by Arnold and Longley for support
- Assertion made that the paper has inaccuracies and misrepresentations
- Rebuttal sent to W3C CCG with supporting documentation
- Encourages reading both sources before deciding on credential security
Misunderstanding About Credential Formats (AnonCreds vs. VC Spec)
- Differences in how “credential” is defined between AnonCreds and VC spec
- AnonCreds’ internal “credentials” are not designed for sharing or verification
- Verifiable AnonCreds “proofs” should be evaluated as verifiable credentials
- Interoperability work focuses on proofs, not credential formats per se
- Mapping between AnonCreds proofs and VC data model already exists
- Lack of willingness to alter UX and messaging may hinder interoperability
Prior Work
-
How is IDEMix Implemented?
Identity Mixer is not directly (re)implemented by Sovrin, but its cryptographic foundations are very similar, and Sovrin’s implementation includes most of its extended features (predicates, multi-credential, revocation, advanced issuance…). One of the researchers who helped to create Identity Mixer is on Sovrin’s Technical Governance Board and has offered insight to keep the implementations aligned on goals and methods.
- IDEMIX Blog
- ABC4Trust—Attribute-based Credentials for Trust
- Concepts and Features of Privacy-Preserving Attribute-Based Credentials
- Concepts and Languages for Privacy-Preserving Attribute-Based Authentication