WebAuthN - W3C
Main
- Why WebAuthn will change the world From: Microsoft By: Pamela Dingle Type: Post Date: 2019-04-19
- W3C finalizes Web Authentication (WebAuthn) standard - ZDNet From: ZDNet Type: Post Date: 2019-03-04
- All about FIDO2, CTAP2 and WebAuthn From: Microsoft Type: Post Date: 2018-11-20
- To Understand WebAuthn, Read CredMan From: Microsoft Type: Post Date: 2019-02-15
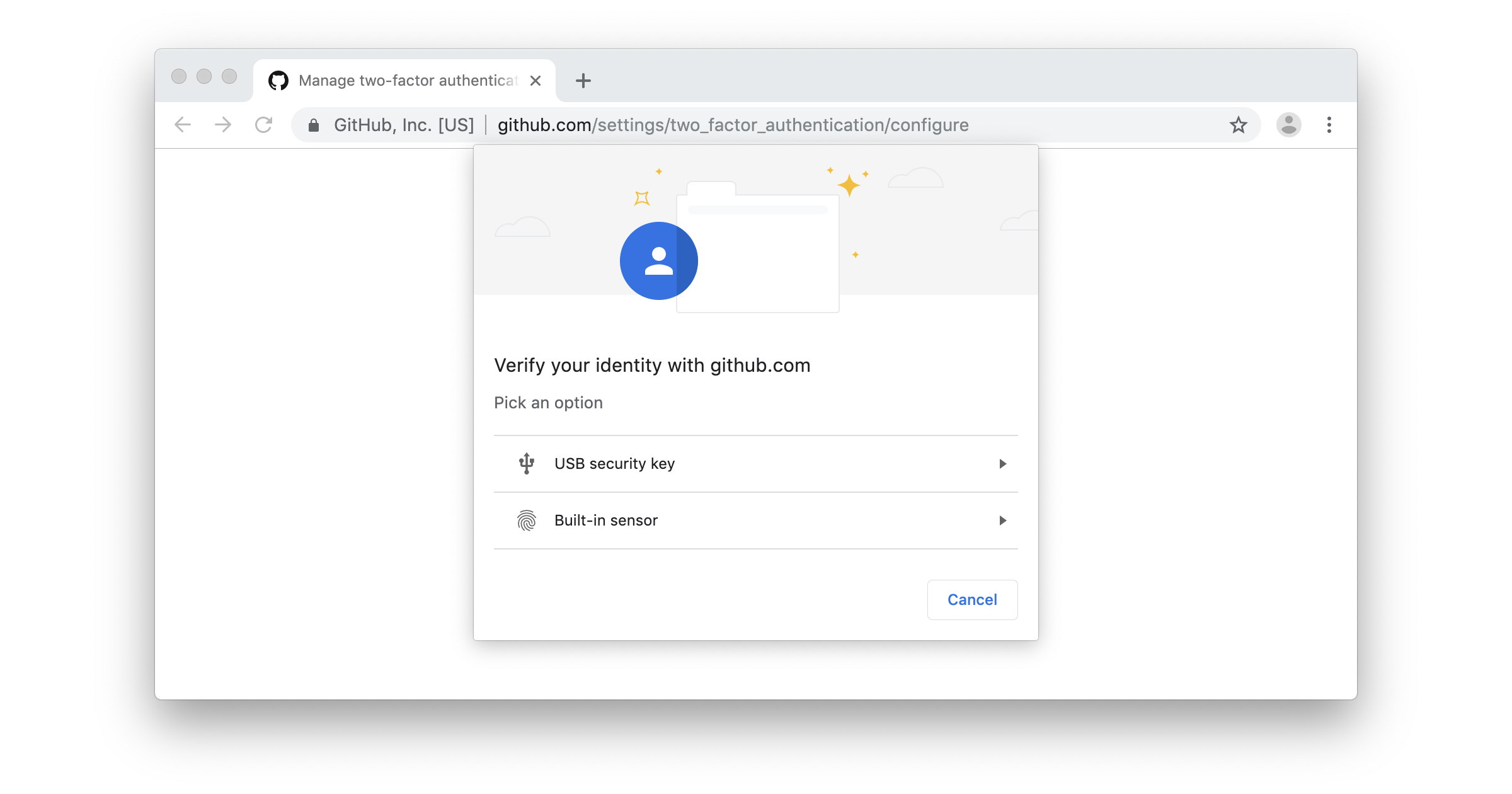
- GitHub supports Web Authentication (WebAuthn) for security keys From: GitHub By: Lucas Garron Type: Post Date: 2019-08-21
- WebAuthn Workshop From: Fido Alliance Type: Presentation Date: 2018-06-07

- WebAuthn Awesome Awesome By: Ackermann Yuri Type: List Date: 2023-04-06
- Guide to Web Authentication From: WebAuthN Guide Type: Page
- Web Authentication (WebAuthn) Credential and Login Demo From: Auth0 Type: Page
A little over a month ago, W3C WebAuthn became a real internet specification. Most of you don’t know what WebAuthn is yet, but many of you will feel the impact in short order. In fact, I will go so far as to say that WebAuthn may change how we all authenticate to the resources we use every day.
We live in a world where the best parts of our individual local hardware and software collection are rarely leveraged to make cloud security decisions. This is because there has never been a vendor-agnostic and privacy-preserving way for cloud resources to interact with individual hardware configurations in any generic way. Until now!
With WebAuthn, any web entity can call a simple Javascript API and ask for a cryptographically secure credential. What happens next is pretty cool – the world’s browsers have worked with the world’s operating system makers and the world’s hardware manufacturers, so that when a website asks for a credential, the browsers work with the underlying platform to securely locate compliant local hardware and talk to it!
WebAuthn allows users to register and authenticate on websites or mobile apps using an “authenticator” instead of a password.
The “authenticator” can be a hardware security key that the user has connected to his computer or a biometric ID that can be acquired from the PC or smartphone’s sensors –such as fingerprints, face scans, iris scans, and others.
This is a great week to be working in Identity Standards, as we at Microsoft celebrate the release of our first ever WebAuthn Relying Party. This one relying party enables standards-based passwordless authentication at Xbox, Skype, Outlook.com and more. But what are the actual pieces of the puzzle and how do they fit? Read on for the big picture of how the W3C WebAuthn and FIDO2 CTAP2 specifications interact. We will start with the industry standards perspective, and then at the end we will summarize how Microsoft implements the various roles.
To understand how FIDO2 authenticators work, you need knowledge of two specifications in two different standards bodies. The WebAuthentication (aka WebAuthn) spec lives at W3C (where the browser makers meet) while the Client-to-Authenticator (aka CTAP2) spec lives at the FIDO Alliance (where hardware and platform folks have joined to solve the problem of Fast IDentity Online).
The holidays are well and truly over, time to get serious - now is the perfect time to read specifications! If you are planning to read the WebAuthn specification, you can ease into the terminology in a simple way - take a cruise through the W3C Credential Management (aka CredMan) specification first. CredMan sets up the object model for the Credential object model that WebAuthn’s PublicKeyCredential extends. This post will be an overview of the CredMan spec, geared for folks who want to call the API as clients, not for those few and proud who are tasked with implementation of the API within a user agent.
GitHub now supports Web Authentication (WebAuthn) for security keys—the new standard for secure authentication on the web. Starting today, you can use security keys for two-factor authentication on GitHub with even more browsers and devices. And, since many browsers are actively working on WebAuthn features, we’re excited about the potential for strong and easy-to-use authentication options for the entire GitHub community in the future.
A curated list of awesome WebAuthn/FIDO2 resources
Passwords have an ever-growing list of problems associated with them, both for users and developers. Users have to worry about passwords being stolen by phishing tools, or their passwords being leaked online if websites they have accounts with are compromised. They have to worry about creating and remembering passwords without dedicated password management tools. Developers have to worry about all the complications of passing passwords through systems and safely storing them in databases.
Web Authentication is a W3C recommendation for defining an API enabling the creation and use of strong, attested, scoped, public key-based credentials by web applications, for the purpose of strongly authenticating users.
Web Authentication works hand in hand with other industry standards such as Credential Management Level 1 and FIDO 2.0 Client to Authenticator Protocol 2.
Auth0 allows you to quickly setup Multi-Factor Authentication with WebAuthn
FIDO Alliance
- FIDO2: WebAuthn & CTAP From: FIDO Alliance Type: Page
- FIDO2: Web Authentication (WebAuthn) From: FIDO Alliance Type: Page
The FIDO Alliance developed FIDO Authentication standards based on public key cryptography for authentication that is more secure than passwords and SMS OTPs, simpler for consumers to use, and easier for service providers to deploy and manage. FIDO Authentication enables password-only logins to be replaced with secure and fast login experiences across websites and apps.
Web Authentication (WebAuthn), a core component of FIDO Alliance’s FIDO2 set of specifications, is a web-based API that allows websites to update their login pages to add FIDO-based authentication on supported browsers and platforms. FIDO2 enables users to leverage common devices to easily authenticate to online services in both mobile and desktop environments.
Working Group
- Web Authentication Working Group From: WebAuthNWG Related: W3C Type: Working group Established: 2016-02-08
- Web Authentication: An API for accessing Public Key Credentials From: WebAuthNWG Related: W3C Type: Specification Date: 2023-05-17
- Web Authentication Working Group Charter From: WebAuthNWG By: Samuel Weiler Type: Post Date: 2019-10-15
The mission of the Web Authentication Working Group, in the Security Activity is to define a client-side API providing strong authentication functionality to Web Applications.
This specification defines an API enabling the creation and use of strong, attested, scoped, public key-based credentials by web applications, for the purpose of strongly authenticating users. Conceptually, one or more public key credentials, each scoped to a given WebAuthn Relying Party, are created by and bound to authenticators as requested by the web application. The user agent mediates access to authenticators and their public key credentials in order to preserve user privacy. Authenticators are responsible for ensuring that no operation is performed without user consent. Authenticators provide cryptographic proof of their properties to Relying Parties via attestation. This specification also describes the functional model for WebAuthn conformant authenticators, including their signature and attestation functionality.
The Web Authentication Working Group will develop recommendation-track specifications defining an API, as well as signature and attestation formats which provide an asymmetric cryptography-based foundation for authentication of users to Web Applications.
Overall goals include obviating the use of shared secrets, i.e. passwords, as authentication credentials, facilitating multi-factor authentication support as well as hardware-based key storage while respecting the Same Origin Policy (SOP) by default and allowing for explicit, constrained SOP relaxation.