Rebooting Web Of Trust - Papers and Advance Readings Index
-
White Papers, Specifications & Proofs of Concept
Our goal for this initial #RebootingWebOfTrust design workshop is to:
- Focus on the creation of the next generation of decentralized web-of-trust based identity systems.
- To generate 5 technical white papers on topics decided by the group that will have the greatest impact on the future”
To this end, I thought it would be useful to define what is a white paper, and as some people desire to go beyond this, what is a specification and proof of concept code.
- WebOfTrust.info - Upcoming Events
See the WebofTrust.Info or github.com/WebOfTrustInfo for more information.
‘Web of Trust’ is a network of relationships that attest to our identity claims. Each party attesting to your identity information becomes a strand in your web of trust.

Selected ‘Rebooting Web of Trust’ Whitepapers
Primers
- A Primer on Functional Identity by Joe Andrieu
- A Primer on Self-Sovereign identity by Christopher Allen & Shannon Appelcline
- DID Primer by Drummond Reed & Manu Sporny
- A Verifiable Claims Primer by Manu Sporny
- Framework for the Comparison of Identity Systems by Kyle Den Hartog
RWoT Workshop Related
-
White Papers, Specifications & Proofs of Concept
Our goal for this initial #RebootingWebOfTrust design workshop is to:
- Focus on the creation of the next generation of decentralized web-of-trust based identity systems.
- To generate 5 technical white papers on topics decided by the group that will have the greatest impact on the future”
To this end, I thought it would be useful to define what is a white paper, and as some people desire to go beyond this, what is a specification and proof of concept code.
- Rebranding the Web of Trust Original RWoT whitepaper
- WebofTrust.info/papers.html
Use Cases
- Amira 1.0
- Re-Imagining What Users Really Want
- Joram 1.0.0
- Powering the Physician-Patient Relationship with HIE of One Blockchain Health IT
- Protecting Digital Identities in Developing Countries
- Opportunities Created by the Web of Trust for Controlling and Leveraging Personal Data
Completed Papers
Rebooting the Web of Trust I

The first Rebooting the Web of Trust design workshop, held in San Francisco, CA - November 3rd & 4th, 2015.
-
Rebranding the Web of Trust
- A history of the Web of Trust and a look at what the term could mean for the future.
- Shannon Appelcline, Dave Crocker, Randall Farmer, and Justin Newton
The Web of Trust is a buzzword for a new model of decentralized self-sovereign identity. It’s a phrase that dates back almost twenty-five years, the classic definition derives from PGP […] the vibrant blockchain community is also drawing new attention to the concept we aim to reboot it.
- Shannon Appelcline, Dave Crocker, Randall Farmer, and Justin Newton
- A history of the Web of Trust and a look at what the term could mean for the future.
-
Opportunities Created by the Web of Trust for Controlling and Leveraging Personal Data
- Five use cases, from two relatively simple cases of managing selective disclosure to the most extreme case of establishing government-verifiable credentials from nothing for a stateless refugee.
- du5t, Kaliya “Identity Woman” Young (@identitywoman), John Edge, Drummond Reed, and Noah Thorp
- Five use cases, from two relatively simple cases of managing selective disclosure to the most extreme case of establishing government-verifiable credentials from nothing for a stateless refugee.
-
Decentralized Public Key Infrastructure
- A massive overview of a decentralized public-key infrastructure (DPKI).
- Christopher Allen, Arthur Brock, Vitalik Buterin, Jon Callas, Duke Dorje, Christian Lundkvist, Pavel Kravchenko, Jude Nelson, Drummond Reed, Markus Sabadello, Greg Slepak, Noah Thorp, and Harlan T Wood
- A massive overview of a decentralized public-key infrastructure (DPKI).
-
Smart Signatures
- A system to explicitly outline and fully program conditions for verification, inspired by Bitcoin Script.
- Christopher Allen, Greg Maxwell, Peter Todd, Ryan Shea, Pieter Wuille, Joseph Bonneau, Joseph Poon, and Tyler Close
- A system to explicitly outline and fully program conditions for verification, inspired by Bitcoin Script.
-
Creating the New World of Trust
- A summary of the next step for the Rebooting the Web of Trust group.
- Shannon Appelcline
- A summary of the next step for the Rebooting the Web of Trust group.
Rebooting the Web of Trust II - ID2020

The second Rebooting the Web of Trust design workshop, in San Francisco, CA, on May 21st & 22nd, 2016. It was run in conjunction with the UN ID2020 Summit on Identity, which occurred at the UN in New York on May 20th, 2016.
-
Identity Crisis: Clearer Identity Through Correlation
- A new way to look at identity, as correlation over time.
- Joe Andrieu, Kevin Gannon, Igor Kruiper, Ajit Tripathi, and Gary Zimmerman
- A new way to look at identity, as correlation over time.
-
Powering the Physician-Patient Relationship with HIE of One Blockchain Health IT
- Using Blockchains and DIDs for physician-patient interactions.
- Adrian Gropper, MD
- Using Blockchains and DIDs for physician-patient interactions.
-
Protecting Digital Identities in Developing Countries
- A real-world use case, describing issues of identity in the developing world.
- Wayne Hennessy-Barrett
- A real-world use case, describing issues of identity in the developing world.
-
Requirements for DIDs (Decentralized Identifiers)
- The first of a series of papers abou tproducing a concrete DID system.
- Drummond Reed and Les Chasen
- The first of a series of papers abou tproducing a concrete DID system.
-
Smarter Signatures: Experiments in Verifications
- A look at uses and requirements of next-generation smart signature systems.
- Christopher Allen and Shannon Appelcline
- A look at uses and requirements of next-generation smart signature systems.
Rebooting the Web of Trust III

The design workshop exceeded its mandate by producing seven papers:
-
DID (Decentralized Identifier) Data Model and Generic Syntax 1.0 Implementer’s Draft 01
- The complete draft of the Decentralized IDentifier (DID) model and syntac, a project that has run through the RWOT workshops to date.
- Drummond Reed, Les Chasen, Christopher Allen, and Ryan Grant
- The complete draft of the Decentralized IDentifier (DID) model and syntac, a project that has run through the RWOT workshops to date.
-
Digital Verification Advancements at RWoT III
- A short overview of enhancements to Digital Verification that came out of RWOT III.
- Manu Sporny with Christopher Allen, Harlan Wood, and Jason Law
- A short overview of enhancements to Digital Verification that came out of RWOT III.
-
Embedding Human Wisdom in Our Digital Tomorrow
- A discussion of the dangers of transferring wisdom into the digital world, seen through the lenses of vulnerability, shadows, healing, tensions, complexity and gestalt, and organizational choices.
- Daniel Hardman, Kaliya “Identity Woman” Young, and Matthew Schutte
- A discussion of the dangers of transferring wisdom into the digital world, seen through the lenses of vulnerability, shadows, healing, tensions, complexity and gestalt, and organizational choices.
-
Hubs
- An overview of the hubs datastore system.
- Daniel Buchner, Wayne Vaughan, and Ryan Shea
- An overview of the hubs datastore system.
-
Joram 1.0.0
- An Information Lifecycle Engagement Model that offers a use case for a Syrian refugee.
- Joe Andrieu and Bob Clint
- An Information Lifecycle Engagement Model that offers a use case for a Syrian refugee.
-
Portable Reputation Toolkit Use Cases
- A model and proof-of-concept implementation for decentralized verification.
- Christopher Allen, Tim Daubenschütz, Manu Sporny, Noah Thorp, Harlan Wood, Glenn Willen, and Alessandro Voto
- A model and proof-of-concept implementation for decentralized verification.
-
Smart Consent Protocol
- Bringing together COALA IP and Consent to deal with digital intellectual property.
- Dr. Shaun Conway, Lohan Spies, Jonathan Endersby, and Tim Daubenschütz
- Bringing together COALA IP and Consent to deal with digital intellectual property.
Rebooting the Web of Trust IV

The fourth Rebooting the Web of Trust design workshop ran in Paris, France, on April 19th-21st, 2017.
-
Design Considerations for Decentralized Reputation Systems
- Angus Champion de Crespigny, Dmitry Khovratovich, Florent Blondeau, Klara Sok, Philippe Honigman, Nikolaos Alexopoulos, Fabien Petitcolas, and Shaun Conway
-
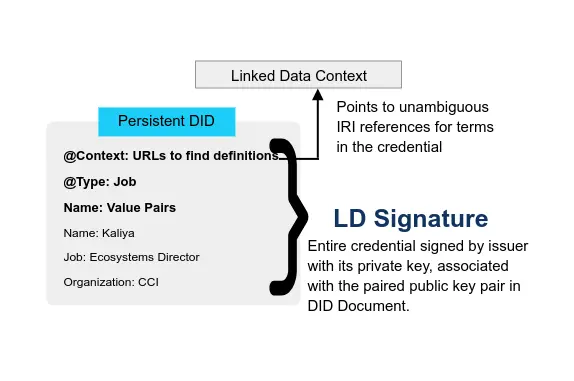
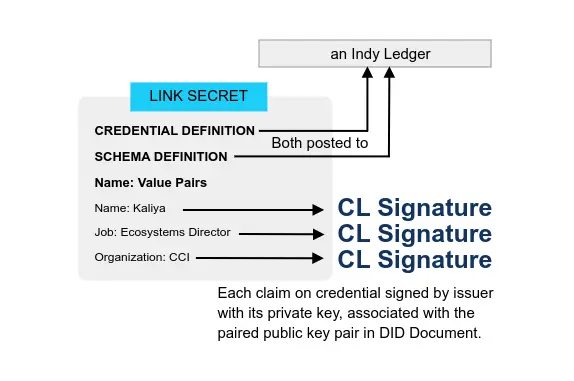
LD Signature Format Alignment - Bringing JSON-LD signatures into alignment with JOSE JSON Web Signature (JWS) standards.
- Kim Hamilton Duffy, Rodolphe Marques, Markus Sabadello, and Manu Sporny
-
Re-Imagining What Users Really Want - Five people, five opportunities for self-sovereign identity.
- Joe Andrieu, Frederic Engel, Adam Lake, Moses Ma, Olivier Maas, and Mark van der Waal.
Rebooting the Web of Trust V

-
ActivityPub: From Decentralized to Distributed Social Networks
- Christopher Lemmer Webber & Manu Sporny
- An overview of the W3C ActivityPub protocol.
-
Amira 1.0.0
- Joe Andrieu & Team
- This paper […] presents a human-centric illustration of an individual’s experience in a self-sovereign, decentralized realization of the Web of Trust as originally conceived by Phil Zimmerman for PGP.
-
The DCS Theorem
- Greg Slepak & Anya Petrova
- A probability proof of the DCS Triangle. Why can’t decentralized consensus systems have all three of decentralization, consensus, and scale? Plus, two methods for getting around these limitations.
-
A Decentralized Approach to Blockcerts Credential Revocation
- João Santos & Kim Hamilton Duffy
- Blockcerts are blockchain-anchored credentials with a verification process designed to be decentralized and trustless. This proposal describes an alternate method of issuing Blockcerts using Ethereum, which allows for a new form of revocation by either the issuer or the recipient.
-
Engineering Privacy for Verified Credentials: In Which We Describe Data Minimization, Selective Disclosure, and Progressive Trust
- Lionel Wolberger, Brent Zundel, Zachary Larson, Irene Hernandez & Katryna Dow
- we have identified three related but distinct privacy enhancing strategies: “data minimization,” “selective disclosure,” and “progressive trust.” These enhancements are enabled with cryptography. The goal of this paper is to enable decision makers, particularly non-technical ones, to gain a nuanced grasp of these enhancements along with some idea of how their enablers work.
-
Identity Hubs Capabilities Perspective
- by Adrian Gropper, Drummond Reed & Mark S. Miller
Identity Hubs as currently proposed in the Decentralized Identity Foundation (DIF) are a subset of a general Decentralized Identifier (DID) based user-controlled agent, based on ACLs rather than an object-capabilities (ocap) architecture. Transitioning the Hubs design to an ocap model can be achieved by introducing an UMA authorization server as the control endpoint.
- by Adrian Gropper, Drummond Reed & Mark S. Miller
-
Linked Data Capabilities
- Christopher Lemmer Webber & Mark S. Miller
Linked Data Signatures enable a method of asserting the integrity of linked data documents that are passed throughout the web. The object capability model is a powerful system for ensuring the security of computing systems.
- Christopher Lemmer Webber & Mark S. Miller
-
Veres One DID Method
- Manu Sporny & Dave Longley
The Veres One Ledger is a permissionless public ledger designed specifically for the creation and management of decentralized identifiers (DIDs). This specification defines how a developer may create and update DIDs in the Veres One Ledger.
- Manu Sporny & Dave Longley
-
When GDPR becomes real, and Blockchain is no longer Fairy Dust
- Marta Piekarska, Michael Lodder, Zachary Larson & Kaliya Young (Identity Woman)
This document describes the GDPR requirements and the different approaches to digital identity solutions and finally explains why distributed ledger technology may offer an opportunity for enterprises to simplify data management solutions that are GDPR compliant.
- Marta Piekarska, Michael Lodder, Zachary Larson & Kaliya Young (Identity Woman)
Rebooting the Web of Trust VI

The sixth Rebooting the Web of Trust design workshop ran in Santa Barbara, California, on March 6th to 8th, 2018.
-
BTCR DID Resolver Specification
- Kim Hamilton Duffy, Christopher Allen, Ryan Grant, and Dan Pape
This describes the process of resolving a BTCR DID into a DID Document. The draft reference implementation is available at https://github.com/WebOfTrustInfo/btcr-did-tools-js (see didFormatter.js). Note that not all steps described in this document are implemented yet.
- Kim Hamilton Duffy, Christopher Allen, Ryan Grant, and Dan Pape
-
Decentralized Autonomic Data (DAD) and the three R’s of Key Management
- by Samuel M. Smith Ph.D. with Vishal Gupta
This paper proposes a new class of data called decentralized autonomic data (DAD). The term decentralized means that the governance of the data may not reside with a single party. A related concept is that the trust in the data provenance is diffuse in nature. Central to the approach is leveraging the emerging DID (decentralized identifier) standard. The term autonomic means self-managing or self-regulating. In the context of data, we crystalize the meaning of self-managing to include cryptographic techniques for maintaining data provenance that make the data self-identifying, self-certifying, and self-securing. Implied thereby is the use of cryptographic keys and signatures to provide a root of trust for data integrity and to maintain that trust over transformation of that data, e.g. provenance. Thus key management must be a first order property of DADs. This includes key reproduction, rotation, and recovery. The pre-rotation and hybrid recovery methods presented herein are somewhat novel.
- by Samuel M. Smith Ph.D. with Vishal Gupta
-
Decentralized Identifiers v1.0
- A Status Note
The Decentralized Identifiers specification editors and implementers spent some time at Rebooting the Web of Trust 6 processing the remaining issues in the issue tracker. This document summarizes the proposed resolutions that the group has put forward to resolve all of the DID specification issues that were submitted before 2018-03-05.
-
Exploring Sustainable Technology Commons using Appreciative Inquiry
- by Heather Vescent, Kaliya “Identity Woman” Young, Adrian Gropper, and Juan Caballero
Technology commons come in a variety of flavors and have achieved varying levels of financial success. For-profit corporate activities have in few historical cases been set up with a financial feedback mechanism to support the commons upon which they depend and capitalize. Why do the commons and the technology sectors’ available forms of capitalism act as incompatible as oil and water, even though they support each other’s aims? When capitalist benefactors support the technology commons that they utilize, it creates a sustainable and thriving commons which enables and supports additional capitalistic technology innovation. Having worked on both sides of the equation, the authors of this piece propose a vocabulary to nourish these interactions between the two sides; identified characteristics of a sustainable technology commons; identified commons models and variations; applied Appreciative Inquiry principles to one commons model; and identified future research areas.
-
Identity Hub Attestation Flows and Components
- by Daniel Buchner, Cherie Duncan, John Toohey, Ron Kreutzer, and Stephen Curran
In this document, we define a set of user flows and describe the associated Action Objects that support a Hub-centric approach to the request, issuance, presentation, verification, and revocation of interoperable attestations. This document extends the Identity Hub Explainer.
-
Introduction to DID Auth
- by Markus Sabadello, Kyle Den Hartog, Christian Lundkvist, Cedric Franz, Alberto Elias, Andrew Hughes, John Jordan & Dmitri Zagidulin
The term DID Auth has been used in different ways and is currently not well-defined. We define DID Auth as a ceremony where an identity owner, with the help of various components such as web browsers, mobile devices, and other agents, proves to a relying party that they are in control of a DID. This means demonstrating control of the DID using the mechanism specified in the DID Document’s “authentication” object. This could take place using a number of different data formats, protocols, and flows. DID Auth includes the ability to establish mutually authenticated communication channels and to authenticate to web sites and applications. Authorization, Verifiable Credentials, and Capabilities are built on top of DID Auth and are out of scope for this document. This paper gives on overview of the scope of DID Auth, supported protocols and flows, and the use of components of the DID Documents that are relevant to authentication, as well as formats for challenges and responses.
-
Open Badges are Verifiable Credentials
- By Nate Otto & Kim Hamilton Duffy
We identify use cases and requirements that connect threads of work happening in the Rebooting Web of Trust community around: educational achievement claims (particularly using the Open Badges vocabulary); use of decentralized identifiers (DIDs) within web services where educational claims circulate; and integrating blockchain-reliant verification layers. We illustrate each of these cases with a set of example documents and describe user stories for Open Badges ecosystem software in the roles of Issuer, Host/Backpack, Displayer, and Verifier that need to be implemented in order to enable the capabilities described.
-
SSI: A Roadmap for Adoption
- By Moses Ma, Claire Rumore, Dan Gisolfi, Wes Kussmaul & Dan Greening (Senex Rex)
This document proposes the formation of a short-term team to develop consistent messaging for the Self-Sovereign Identity (SSI) market. It will target key stakeholders who would actively promote SSI adoption. The goal is to create an SSI market roadmap. This roadmap will help SSI leaders, standards bodies, developers, academics, media, and investors coordinate and clarify their messaging for the market, to accelerate the SSI adoption.
Rebooting the Web of Trust VII

The seventh Rebooting the Web of Trust design workshop, ran near Toronto, Canada, on September 26th to 28th, 2018.
-
BTCR v0.1 Decisions (Text)
- Kim Hamilton Duffy, Christopher Allen, and Dan Pape
The Bitcoin Reference (BTCR) DID method supports DIDs using the Bitcoin blockchain. This method has been under development through Rebooting Web of Trust events and hackathons over the past year. The BTCR method’s reliance on the Bitcoin blockchain presents both advantages and design challenges. During RWOT7, the authors made a number of design and implementation decisions – largely scope-cutting in nature – in order to lock down a Minimum Viable Product (MVP) version, which we’ll refer to as v0.1. This paper documents those decisions, which will apply to the upcoming v0.1 BTCR method specification and associated v0.1 BTCR reference implementation.
-
A DID for Everything (Text)
- Shaun Conway, Andrew Hughes, Moses Ma, Jack Poole, Martin Riedel, Samuel M. Smith Ph.D., and Carsten Stöcker
The decentralized identifier (DID) is a new and open standard type of globally unique identifier that offers a model for lifetime-scope portable digital identity that does not depend on any centralized authority and that can never be taken away by third-parties. DIDs are supported by the W3C community and the Decentralized Identity Foundation (DIF). They are the “atomic units” of a new layer of decentralized identity infrastructure. However, DIDs can be extended from identifiers for people to any entity, thus identifying everything. We can use DIDs to help us identify and manage objects, machines, or agents through their digital twins; we can expand them to locations, to events, and even to pure data objects, which we refer to as decentralized autonomic data (DAD) items.
The paper will present novel use-cases for DIDs and DADs and propose a new cryptographic data structure that is a self-contained blockchain of DADs. This enables the verification of the provenance of a given data flow. It builds on a prior paper and an associated reading.
-
How to Convince Dad* of the Importance of Self-Sovereign Identity (Text)
- Shannon Appelcline, Kenneth Bok, Lucas Parker, Peter Scott, and Matthew Wong
One of the major problems with bootstrapping self-sovereign identity is that it requires adoption by a large number of people. Pushing self-sovereign identity from the top-down is most likely to result in a technology that’s not actually used, but instead encouraging the average person to demand self-sovereign identity from the bottom-up will result in the organic development of a vibrant, well-utilized decentralized web-of-trust ecosystem.
This paper addresses that need by offering arguments to a variety of people who might be reluctant to use self-sovereign identity, uninterested in its possibilities, or oblivious to the dangers of centralization. By focusing on the needs of real people, we hope to also encourage developers, engineers, and software business owners to create the apps that will address their reluctance and fulfill their needs, making self-sovereign identity a reality.
-
IPLD as a general pattern for DID documents and Verifiable Claims (Text)
- jonnycrunch, Anthony Ronning, Kim Duffy, Christian Lundkvist
Since the emergence of the Decentralized Identifier (DID) specification at the Fall 2016 Rebooting the Web of Trust [1], numerous DID method specifications have appeared. Each DID method specification defines how to resolve a cryptographically-tied DID document given a method-specific identifier. In this paper, we describe a way to represent the DID document as a content-addressed Merkle Directed Acyclic Graph (DAG) using Interplanetary Linked Data (IPLD). This technique enables more cost-efficient, scaleable creation of DIDs and can be applied across different DID method specifications.
-
Peer to Peer Degrees of Trust (Text)
- Harrison Stahl, Titus Capilnean, Peter Snyder, and Tyler Yasaka
Aunthenticity is a challenge for any identity solution. In the physical world, at least in America, it is not difficult to change one’s identity. In the digital world, there is the problem of bots. The botnet detection market is expected to be worth over one billion USD by 2023, in a landscape where most digital activity is still heavily centralized. These centralized digital solutions have the advantage of being able to track IP addresses, request phone verification, and present CAPTCHAs to users in order to authenticate them. If this problem is so difficult to solve in the centralized world, how much more challenging will it be in the decentralized world, where none of these techniques are available?
In this paper, we explore the idea of using a web of trust as a tool to add authenticity to decentralized identifiers (DIDs). We define a framework for deriving relative trust degrees using a given trust metric: a “trustworthiness” score for a given identity from the perspective of another identity. It is our intent that this framework may be used as a starting point for an ongoing exploration of graph-based, decentralized trust. We believe this approach may ultimately be used as a foundation for decentralized reputation.
-
Resource Integrity Proofs (Text)
- Ganesh Annan and Kim Hamilton Duffy
Currently, the Web provides a simple yet powerful mechanism for the dissemination of information via links. Unfortunately, there is no generalized mechanism that enables verifying that a fetched resource has been delivered without unexpected manipulation. Would it be possible to create an extensible and multipurpose cryptographic link that provides discoverability, integrity, and scheme agility?
This paper proposes a linking solution that decouples integrity information from link and resource syntaxes, enabling verification of any representation of a resource from any type of link. We call this approach Resource Integrity Proofs (RIPs). RIPs provide a succinct way to link to resources with cryptographically verifiable content integrity. RIPs can be combined with blockchain technology to create discoverable proofs of existence to off-chain resources.
-
Use Cases and Proposed Solutions for Verifiable Offline Credentials (Text)
- Michael Lodder, Samantha Mathews Chase, and Wolf McNally
In this paper we cover various scenarios where some or all parties have intermittent, unreliable, untrusted, insecure, or no network access, but require cryptographic verification (message protection and/or proofs). Furthermore, communications between the parties may be only via legacy voice channels. Applicable situations include marine, subterranean, remote expeditions, disaster areas, refugee camps, and high-security installations. This paper then recommends solutions for addressing offline deployments.

Topics and Advance Readings
In advance of the design workshop, all participants are requested to produce a one-or-two page topic paper to be shared with the other attendees on either:
- A specific problem that they wanted to solve with a web-of-trust solution, and why current solutions (PGP or CA-based PKI) can’t address the problem?
- A specific solution related to the web-of-trust that you’d like others to use or contribute to?
RWoT 1

-
White Papers, Specifications & Proofs of Concept
Our goal for this initial #RebootingWebOfTrust design workshop is to:
- Focus on the creation of the next generation of decentralized web-of-trust based identity systems.
- To generate 5 technical white papers on topics decided by the group that will have the greatest impact on the future”
To this end, I thought it would be useful to define what is a white paper, and as some people desire to go beyond this, what is a specification and proof of concept code.
-
Advanced Web-of-Trust Concepts
- Christopher Allen @ChristopherA <ChristopherA@LifeWithAlacrity.com>
-
Attempts at common terminology for digital identity systems
- Christian Lundkvist - @ChrisLundkvist <christian.lundkvist@consensys.net>
-
Authorities vs. Peers: Pain Points in Security
- Christopher Allen @ChristopherA <ChristopherA@LifeWithAlacrity.com> & Shannon Appelcline @Appelcline <ShannonA@skotos.net>
-
Avoiding Confused Deputy Attack Using Capabilities
- Tyler Close <tyler.close@gmail.com>
-
Binding Identity in a Decentralized System
- Wayne Thayer @WThayer <wthayer@gmail.com>
-
Blockchain-based Trust for Software Components
- Sean Gilligan @msgilligan <sean@msgilligan.com>
-
Blockchain Tech Opportunities in the Web-of-Trust
- Peter Todd @PeterToddBTC <pete@petertodd.org>
-
Building a Web of Trust for E-commerce
- Michael Folkson @michaelfolkson <michaelfolkson@gmail.com>
-
Cool hack with XDI graphs, blockstore, link contracts, and cryptographic identifiers
- Markus Sabadello @Peacekeeper <markus@projectdanube.org>
-
Dealing with key loss in digital identity systems
- Christian Lundkvist - @ChrisLundkvist <christian.lundkvist@consensys.net>
-
Decentralized Authentication with Blockchain Auth
- Ryan Shea @ryaneshea <ryan@onename.com>
-
Decentralized Cooperation Needs Decentralized Reputation
- Noah Thorp @noahthorp <noah@citizencode.io>
-
Different Models for Trust
- Kaliya Hamlin @IdentityWoman <kaliya@identitywoman.net>
-
Distributed multi-ledger model for financial industry
- Pavel Kravchenko @kravchenkopo <kravchenkopo@gmail.com>
-
Distributed Receptor-Based Computing
- Arthur Brock - @ArtBrock <artbrock@gmail.com>
-
Distributed Trust Systems and the Kenyesian Beauty Contest
- Joel Dietz @fractastical <jdietz@gmail.com>
-
First Encounters with PGP
- Kiara Robles @anarchoass <kiara.robles@gmail.com>
-
Hierarchical Deterministic Keys: BIP32 & Beyond
- Christopher Allen @ChristopherA <ChristopherA@LifeWithAlacrity.com> & Shannon Appelcline @Appelcline <ShannonA@skotos.net>
-
How not to build an Orwellian reputation system
- Juan S. Galt @juansgalt <juans.galt@tuta.io>
-
Identity, Guidance and Situational Awareness
- Matthew Schutte @MatthewJosef <matt@calabs.org>
-
Identity, Property and Simulation
- Patrick Deegan <pdeegan@gmail.com>
-
Key revocation of lost and stolen keys
- Martin Koeppelmann @koeppelmann <martin.koeppelmann@consensys.net >
-
Key Transparency for End Users
- Joseph Bonneau @JosephBonneau <jbonneau@cs.stanford.edu>
-
Knowing When Your Digital Identity Has Been Compromised
- Justin Newton @JustinwNewton <justin@netki.com>
-
Lightning Network and Web of Trust
- Joseph Poon <joseph@lightning.network>
-
Linked Local Names
- Christopher Allen @ChristopherA <ChristopherA@LifeWithAlacrity.com>
-
Modern PKI: Identity Assertions Forming Trust Networks
- Duke Dorje @dukedorje <duke@citizencode.io>
-
PGP Paradigm
- Jon Callas - @JonCallas <jon@crypto.expert> & Phil Zimmerman - <prz@mit.edu>
-
PKI Tools in EVM-based blockchains
- ChristianLundkvist - @ChrisLundkvist <christian.lundkvist@consensys.net>
-
Progressive Trust
- Christopher Allen @ChristopherA <ChristopherA@LifeWithAlacrity.com>
-
Real life application of WoT: Refugee Use Case
- Alicia Carmona <alicia.carmona@id2020.org>
-
Reputation and the Real World
- Randy Farmer @FRandallFarmer <randy.farmer@pobox.com>
-
Schnorr Signatures: An Overview
- Christopher Allen @ChristopherA <ChristopherA@LifeWithAlacrity.com> & Shannon Appelcline @Appelcline <ShannonA@skotos.net>
-
Secret Handshake: Key Exchange as a Capability System
- Dominic Tarr @DominicTarr <dominic.tarr@gmail.com>
-
Secure Naming on the Blockchain
- Muneeb Ali @muneeb <muneeb@onename.com> and Ryan Shea @ryaneshea <ryan@onename.com>
-
Selective Disclosure of Identity with Hierarchical Deterministic Keys and JSON Web Tokens
- Ryan Shea @ryaneshea <ryan@onename.com>
-
Tensions related to identity and community regulation
- Matthew Schutte @MatthewJosef <matt@calabs.org>
-
The Naming of Things
- Matthew Schutte @MatthewJosef <matt@calabs.org>
-
Thin Clients
- Greg Slepak @TaoEffect <hi@okturtles.com>
-
Trust Exchange: An Architecture for a Permanent Open Trust Network
- Harlan T. Wood @HarlanTWood <h@rlan.me >
-
Web of Trust with Blockchain IDs
- Ryan Shea @ryaneshea <ryan@onename.com>
- Christopher Allen @ChristopherA <ChristopherA@LifeWithAlacrity.com>
-
XDI Link Contracts: An Overview
- Drummond Reed @DrummondReed <drummond@respect.network>
- Notes on the IPFS Keychain (or the Web Keychain)
- IPFS - The Permanent Web
- multiplexed: a ‘slightly radical’ framing of identity
-
RLPx: Cryptographic Network & Transport Protocol - Version 0.3
- Alex Leverington
- Self-certifying File System
-
Trust Models, Accountability, LIfeCycle and Social Context
- by Kaliya “Identity Woman” Young (formerly Hamlin)
RWoT ID2020

-
A Double Edge Sword of Having an Identity
- Marta Piekarska <marta@blockstream.io>
-
A Self-Sovereign Identity Architecture
- Manu Sporny @msporny and David Longley
-
Blockstack: Design and Implementation of a Global Naming System with Blockchains
- by Muneeb Ali @muneeb <muneeb@blockstack.com> and Jude Nelson @judecnelson <jude@blockstack.com> and Ryan Shea @ryaneshea <ryan@blockstack.com>
-
From Identity to Refugee Status Determination
- Susan R. Ramonat <SRamonat@seic.com>
-
Peer Attestation of Identity in the Real World
- Dr Shaun Conway & Lohan Spies
-
Sovereign Identity Namespaces
- Drummond Reed @DrummondReed <drummond@respectnetwork.com>
-
Identity System Essentials
- Samuel Smith and Dmitry Khovratovich
-
Decentralized Identifiers (DIDs) and Decentralized Identity Management (DIDM)
- Les Chasen
-
“Immutable Me” - A Discussion Paper Exploring Data Provenance To Enable New Value Chains
- George Samman @sammantic <George.Samman@meeco.me> and Katryna Dow @katrynadow <Katryna.Dow@meeco.me>
-
No Secure Protocol = No Sovereign Identity
- Greg Slepak @taoeffect <hi@okturtles.com>
-
Questions around key management for digital ID systems
- by Christian Lundkvist @chrislundkvist <christian.lundkvist@consensys.net> and Rouven Heck @rh7 <rouven.heck@consensys.net>
-
The Path to Self-Sovereign Identity
- Christopher Allen @ChristopherA <ChristopherA@LifeWithAlacrity.com>
-
Distibuted Identity Management - Verifiable Claims Exchange Via Agents
- Gary Zimmerman
-
Blockstack Rules and Support for Multiple Blockchains
- Muneeb Ali *@muneeb <muneeb@blockstack.com>
-
Plurality of Provenance in Distributed Identity
- Joe Andrieu <joe@joeandrieu.com>
-
Identity is a Phenomenon, Not a Property
- Joe Andrieu <joe@joeandrieu.com>
-
Dex: Deterministic Predicate Expressions for Smarter Signatures
- Peter Todd
-
Scaling a BFT Consensus Protocol for Identity
- Jason Law & Lovesh Harchandani
-
XDI Graphs in IPFS
- Markus Sabadello
-
Replace Blockchain with DLT (Distributed Ledger Technology)
- Erik Anderson
-
Blockchain For Capital Markets
- Erik Anderson
-
Identity Management IdSec
- Erik Anderson
-
Trust-i-ness
- by Kaliya “Identity Woman”
-
ID2020 - Self-Sovereign Identity
- Patrick Deegan
-
Identity and decentralised Communication
- By Harsh Patel
- Chime National Patent ID Challenge
- Usability and Multiplicity in Global Identity Management — by D. Crocker ~ <dcrocker@bbiw.net>
- Decentralized Identity Satoshi Style - by Darrell Duane - <darrell@idi.io>
- Declaration of Identity - Printed.pdf
- Identities for Moving Things - by Daniel Ford - <dan@keoja.com>
- Legalizing Identity Protocols for the United Nations 16.9
- Personal Levels of Assurance (PLOA) — by J. Oliver Glasgow and Jeff Dogen, Kennie Kwong, David Chen, Johannes Jaskolski, Kevin Castellow, Dan Druta — An AT&T Whitepaper on Assurance
- Clues — by Nicola Greco — something that serves to guide or direct in the solution of a problem or mystery.
RWoT 3

-
Identity as Linked Data on Immutable Ledgers
- Tim Daubenschuetz and Trent McConaghy
-
EU General Data Protection Regulation & Self-Sovereign Identifier(s)
- David Robert
-
Identity Forking and Federated Reputation
- Christopher Malon
-
OpenTimestamps: Scalable, Trustless, Distributed Timestamping with Bitcoin
- Peter Todd
-
Distributed Identity, Distributed Self
- Natalie Smolenski
-
Blockchain Extensions for Linked Data Signatures
- the Signature Super Friends (Manu Sporny, Harlan Wood, Noah Thorp, Wayne Vaughn, Christopher Allen, Jason Bukowski, and Dave Longley)
-
Fit for Purpose Blockchains
- Digital Bazaar (Manu Sporny, Dave Longley, Dave Lehn, and Adam Lake)
-
Taxonomy of Identity Interaction Types
- Kaliya Young
-
Privacy Preserving Identity Architectures
- Anonymous (no, not that Anonymous, the other one)
-
A Technlogy-Free Definition of Self-Sovereign Identity
- Joe Andrieu
-
Architecture of Proof-of-Stake Blockchain that Doesn’t Have Native Coin and its Applicability to Decentralized Trading
- Pavel Kravchenko
-
JXD Examples
- Markus Sabadello
-
Anonymous Credentials in Sovrin
- Jason Law and Daniel Hardman
-
Portable Reputation Toolkit
- Noah Thorp and Harlan Wood
-
Blockchain Attestation Taxonomies
- Christian Lundkvist
-
Slepak’s Triangle: The fundamental user limit of decentralized consensus systems
- Greg Slepak (@taoeffect)
-
Sovereign Identity Model for Digital Ecologies
- Patrick Deegan
-
Alternative Futures: Framework for Identity Scenarios
- Alessandro Voto
-
Powering the Physician-Patient Relationship with HIW of One Blockchain Health IT
- Adrian Gropper
-
Creating a Humanized Internet
- Monique Morrow, et al
-
Smart Consent Protocol
- Dr Shaun Conway, Lohan Spies, Jonathan Endersby, Tim Daubenschütz (see Completed Papers III)
-
Creating a Humanized Internet
- Akram Alfawakheeri <akram.f1_1@gmail.com>, Mark Kovarski <mark@kovarski.org>, Aron Dutta <\aron_dutta@yahoo.com>, Monique Morrow <monique.morrow223@gmail.com>, Vivien Shen <vshen670@gmail.com>
-
DIDs and Personal Data Storage for Children
- Jonathan Endersby, Shaun Conway, Lohan Spies
-
BIP32-Ed25519 Hierarchical Deterministic Keys of a Non-Linear Keyspace
- Dmitry Khovratovich, Jason Law
- Sovrin - Digital Identities in the Blockchain Era
-
Alternative Futures: Framework for Identity Scenarios
- by Alessandro Voto
- Blockchain Technologies Feature Analysis -Copyright 2016 Digital Bazaar, Inc.
-
DID (Decentralized Identifier) Specification
- Editors: Drummond Reed, Les Chasen Contributors: Christopher Allen, Manu Sporny, David Longley, Jason Law, Daniel Hardman, Markus Sabadello (see Completed Papers III)
- Towards a User Interface for Selectively Revealing Fine-Grained Personal Information to Transaction Counterparties
- Recovery strategy for user-controlled keys for self-sovereign identity
RWoT 4

- Aligning Signature Formats by Manu Sporny, Christopher Allen, Jason Law, and Ryan Shea
- Beyond Identity Cards by Joe Andrieu
- Blockcerts and Open Badges Signature Alignment by Kim Hamilton Duffy
- Booting a Web of Sovereignty with a Decentralized Social App by Adam Lake
- Certificate Chains for DID-based Self-sovereign Identities by Christian Lundkvist
- Credit-based Reputations for Identity Management with Blockchain and Flow Networks by Tobias Mayer, Obar Hasan, and Lionel Brunie
- DID Auth by James Monaghan
- The DID Family of Specifications by Drummond Reed
- DID Method Specifications / BTCR and PGPR by Ryan Grant
- DID Names by Drummond Reed and James Monaghan
- Distributed Identities as a EU Cross-border Identity Infrastructure by L. Boldrin
- DKMS—Decentralized Key Management System by Drummond Reed
- Fostering the Resilience of an Ecosystem of Workers through Regulated Decentralized Reputation by Philippe Honigman & Klara Sok
- ID-Blockchain: An Initiative towards Privacy-preserving Blockchain-based Identity by Olivier Maas & Florent Poiron
- The IP Blockchain: Enhancing Global Responsiveness to Infectious Disease Outbreaks by Moses Ma, Mark van der Waal, and Net Jacobsson
- Project Vouch: A Decentralized Identity Network Based on Public Attestation, Reputation, and Approval of Identity Attributes by Angus Champion
- Reputation Proofs by Dmitry Khovratovich
- RWoT Proposals and Modern Portable Secure Hardware by Nicolas Bacca
- Self-sovereign Delegated Identity by Pierre Noizat
- Towards a User-centered Web of Trust by Fabien Petitcolas & Paul Dunphy
- Trust for Security and Security for Trust by Nikolaos Alexopoulos
- Verifiable Claims and Web of Trust by Manu Sporny, Christopher Allen, Joe Andrieu, Matthew Collier, Dave Longley, and Adam Lake
- XDI Verifiable Claims and Link Contracts by Markus Sabadello
RWoT 5

The following advanced readings have been prepared as primers, intended to give you a foundation in some of the topics that may be discussed at the design workshop:
- A Primer on Functional Identity by Joe Andrieu
- A Primer on Self-Sovereign identity by Christopher Allen & Shannon Appelcline
- DID Primer by Drummond Reed & Manu Sporny
- A Verifiable Claims Primer by Manu Sporny
- Framework for the Comparison of Identity Systems
Here are the rest of the advance readings to date:
- #RebootingWebOfTrust User Story & Tech Concept by Christopher Allen
- ActivityPub: from decentralized to distributed social networks by Christopher Lemmer Webber
- Architectural Layering for Decentralized Identification by Drummond Reed
- BFTKV: Byzantine Fault Tolerant Web of Trust based Key-Value Storage by Ercan Ozturk
- BFTKV DID Method Specification by Ercan Ozturk
- Biometric transaction signing on blockchain by John Callahan & Virgil Tornoreanu
- Blockchain Based Digital Signatures: Admissibility and Enforceability by Dazza Greenwood
- BTCR DIDs and DDOs by Kim Hamilton Duffy
- Credential Handler API by Dave Longley and Manu Sporny
- Data Minimization and Selective Disclosure by Lionel Wolberger
- Decentralized Identifier Tooling by Dave Longley & Manu Sporny
- DID for the 3D Web by Alberto Elias
- DID Tooling by Manu Sporny and Matt Collier
- First XDI Link Contract between “btcr” DID and “sov” DID by Markus Sabadello
- Framework for the Comparison of Identity Systems by Kyle Den Hartog
- HIE of One Loop: A Patient-Controlled Independent Health Record by Adrian Gropper
- The Horcrux protocol: Biometric credentials as high-privacy verifiable claims by John Callahan & Asem Othman
- Hub Asset Access Control System - Intent by Daniel Buchner
- Hypercerts: Blockcerts Revocation Improvements by João Santos and Kim Hamilton Duffy
- Identifying stakeholders’ challenges in the digital economy by Irene Hernandez
- Open Badges (and Blockcerts) as Verifiable Claims by Kim Hamilton Duffy and Nate Otto
- Owned vs. Unowned Claims and Self-Sovereign Identity by Natalie Smolenski
- Recommendations for Decentralized Key Management Systems by Michael Lodder
-
Trust Objects: Enabling Advanced Reputation Services on the Web of Trust by Moses Ma & Dr. Rutu Mulka
- Original Proposal by Moses Ma & Dr. Rutu Mulka
- Veres One DID Method Specification by Manu Sporny, Dave Longley & Matt Collier
- Verifiable Claims of Impact by Cedric Franz & Dr. Shaun Conway
- Visa? Really? by Kaliya ‘Identity Woman’ Young
- Data Minimization and Selective Disclosure by Lionel Wolberger
- HIE of One Loop: A Patient-Controlled Independent Health Record by Adrian Gropper, MD and the Loop Project Team
RWoT 6

- Attribute Based Credentials and Variable Length Data Graphs by nage
- Blockchain Timestamps Unnecessary In Proof-of-Work? by Greg Slepak
- BTCR DID Resolver by Kim Hamilton Duffy, Christopher Allen, Ryan Grant
- Collegial Certifcation Works for Truly Collegial Communities by Wes Kussmaul
- Credential Providers for Signing Application Requests by Cedric Franz
- DClaims News - A Fake News Mitigation Platform by João Santos
- Decentralized Attestations Storage - Current Challenges by Kulpreet Singh
- Decentralized Identities for the Cannabis Industry by Matthew Nguyen & Nicholas Shook
- Decentralized Interfaces and the Request-Responsive World by Vlad Kahoun
- Decentralized Self-certifying Self-Identifing Data by Samuel M. Smith
- A Demonstration of the Veres One Blockchain by David I. Lehn, Manu Sporny, David Longley, Matt Collier, and Chris Webber
- DID-Auth Protocol by Kyle Den Hartog
- DID Auth: Scope, Formats, and Protocols by Markus Sabadello
- did:erc725 method by Markus Sabadello, Fabian Vogelsteller, and Peter Kolarov pkolarov@finid.me
- Distributed Reputation Systems Using Blockchain Records by Kate Sills
- Hashed PII Question by Identity Woman
- The Horcrux Protocol: A Method for Decentralized Biometric-based Self-sovereign Identity by Asem Othman & John Callahan
- Identity System for Immersive and Ambient Computing by Alberto Elias
- Integrating Identity Silos via Address Books by vishal144
- Open Badges Prototypes and Action Items 2018 by Nate Otto and Kim (Hamilton) Duffy
- Open TLS by Sam Curren
- Open Verifiable Data to Drive the Digital Economy by John Jordan
- Petnames for Self Sovereign and Human Readable Identifiers by Christopher Lemmer Webber
- Proposed Collaboration on Open Standards for Data Wallet and Data Service Integration by Ron Kreutzer
- Recent Happenings with Linked Data Capabilities by Christopher Lemmer Webber
- Self-sovereign Compliance by Moses Ma
- The Three Primary Roles in the Sovrin Web of Trust Model by Drummond Reed
- Towards a Sustainable Technology Commons by Heather Vescent
- Using Blockchain to Store Academic Accreditations by Luiz Gustavo Ferraz Aoqui and Andrei Moskalev
- Veres One Primer by Manu Sporny, et. al.
- The Veres One DID Method by Manu Sporny, David Longley, and Chris Webber
- Veres One Demo by David I. Lehn, et. al.
- Web of Pragmatics: A Comment on Methodology by D. Crocker
RWoT 7

- Addressing Global/Local Barriers to Adoption of Decentralized Identity Systems by Eric Brown
- Agent to Agent Communication Protocol Overview by Kyle Den Hartog
- Blockcerts – Where we are and what’s next by Kim Hamilton Duffy, Anthony Ronning, Lucas Parker, and Peter Scott
- Can Curation Markets Establish a Sustainable Technology Commons by Sam Chase
- CapAuth by Manu Sporny, Dave Longley, Chris Webber, and Ganesh Annan
- A Concept Diagram For RWOT Identity Terms by Andrew Hughes
- Cryptocurrency Wallets as a Form of Functional Identity by Mikerah Quintyne-Collins and Abdulwasay Mehar
- Decentralized Error Reporting by Jack Poole
- Decentralized Identities and eIDAS by Oliver Terbu
- Decentralized Identity: Hub Authentication & Message Encryption by Daniel Buchner
- DIDDoc Conventions for Interoperability by Stephen Curran & Olena Mitovska
- DIDs In DPKI by Greg Slepak
- DID Resolution Topics by Markus Sabadello
- Digital Identity for the Homeless by Matthew Wong, T. Tian & CG Chen
- Exploring Browser Web of Trust Use Cases by Peter Snyder and Ben Livshits
- Five Mental Models of Identity by Joe Andrieu
- Identity Hub Permissions / Authorization by Daniel Buchner
- IPLD as a general pattern for DID Documents by Christian Lundkvist
- Is a Decentralized Collective Identity Possible? by Heather Vescent
- Magenc Magnet URIs: Secure Object Permanence for the Web by Christopher Lemmer Webber
- Measuring Trust by Tyler Yasaka
- More Control for Identity Holders by Arturo Manzaneda and Ismenia Galvao
- Nobody REALLY Trusts the Blockchain by Daniel Burnett
- Not-a-Bot: A Use Case for Decentralized Identity using Proximity Verification to generate a Web of Trust by Moses Ma & Claire Rumore
- The Political Economy of Naming by Kate Sills
- A Public Web of Trust of Public Identities by Ouri Poupko and Ehud Shapiro
- Resource Integrity Proofs by Ganesh Annan, Manu Sporny, Dave Longley, and David Lehn
- RWoT Tribal Knowledge: Cryptographic and Data Model Requirements by Manu Sporny, Dave Longley, and Chris Webber
- The Role of Standards in Accelerating Innovation by Michael B. Jones
- Scoped Presentation Request on Verifiable Credentials by Martin Riedel
- Secure Crypto-Wallet Introductions by Wolf McNally, Ryan Grant
- Standards for Agency and Decentralized Information Governance - Early Experience by Adrian Gropper, MD, Michael Chen, MD, and Lydia Fazzio, MD
- Towards Proof of Person by Peter Watts
- A Trustless Web-of-Trust by Ouri Poupko
- Verifiable Displays by Kim Hamilton Duffy, Lucas Parker & Anthony Ronning
- Verifiable Offline Credentials by Michael Lodder
- What (and Who) Is In Your Wallet by Darrell O’Donnell
- Digital Identity for the Homeless by Matthew Wong, T. Tian & CG Chen
- Zero Trust Computing with DIDs and DADs by Samuel M. Smith
License
Unless otherwise noted, all RWoT Completed Papers, Topics and Advance Readings are licensed Creative Commons CC-BY.
RWoT Github Listing
- WebOfTrustInfo/self-sovereign-identity - Articles and documents associated with designing and implementing identity technology using self-sovereign identity principles
- WebOfTrustInfo/website - Website for http://www.WebOfTrust.info
- WebOfTrustInfo/community-resilience - Rebooting Web of Trust Community Resilience Team
- WebOfTrustInfo/satyrn - A Markdown-based JavaScript Sandbox
-
WebOfTrustInfo/sss - Library for the Shamir secret sharing scheme
- Forked from dsprenkels/sss
- WebOfTrustInfo/verifiable-news - TBD: W3C Credentials Community Group repository for curbing “social bots” and mitigating the spread of online misinformation and “fake news”.
- WebOfTrustInfo/portable-reputation-toolkit
Workshops
- Rebooting the Web of Trust I: San Francisco (November 2015)
- Rebooting the Web of Trust II: ID2020 (May 2016)
- Rebooting the Web of Trust III: San Francisco (October 2016)
- Rebooting the Web of Trust IV: Paris (April 2017)
- Rebooting the Web of Trust V: Boston (October 2017)
- Rebooting the Web of Trust VI: Santa Barbara (March 2018)
- Rebooting the Web of Trust VII: Toronto (September 2018)