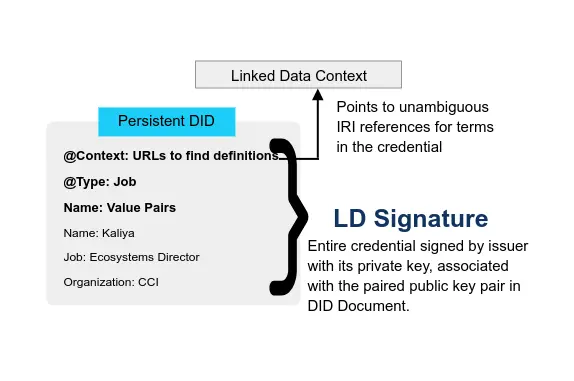
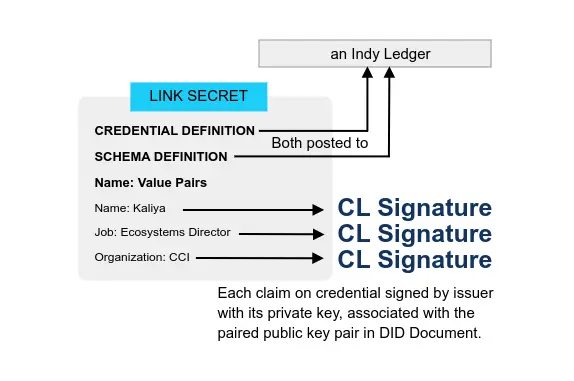
Microsoft Identity
Company
Name: Microsoft
Main: Website, Blog, Socials: Twitter, Youtube, Crunchbase, Linkedin, Related: DIF, ID2020, ID2020 Founder, VCI Founder Founders: Bill Gates, Paul Allen, Subur Khan Founded: 1975 Location: USA, Washington, Redmond Sector: Enterprise Market: IT, IAM, ID, SSI Projects: VCI Standard: WebAuthN, Secure Data StorageMicrosoft enables digital transformation for the era of an intelligent cloud and an intelligent edge. Its mission is to empower every person and every organization on the planet to achieve more.
Product
- DTDL models - Azure Digital Twins Type: Docs Date: 2023-04-05 Market: IOT Standard: DTDL, JSON-LD
- Azure Documentation Type: Documentation Date: 2023-02-25
- Microsoft Entra Verified ID documentation Type: Docs Date: 2023-01-24 Tech: Entra Standard: Verifiable Credentials
- Microsoft Entra Verified ID. Verify once. Use everywhere Type: Product Date: 2023-01-01 Standard: Verifiable Credentials
- Configure your tenant for Microsoft Entra Verified ID Type: Docs Date: 2022-11-16 Tech: Entra
- Issue Azure AD Verifiable Credentials from an application Type: Docs Date: 2022-11-16 Tech: Entra, AzureAD
- Set up Azure Blob Storage for storing your Azure AD Verifiable Credentials configuration files.
- Create and upload your Verifiable Credentials configuration files.
- Create the verified credential expert card in Azure.
- Gather credentials and environment details to set up the sample application.
- Download the sample application code to your local computer.
- Update the sample application with your verified credential expert card and environment details.
- Run the sample application and issue your first verified credential expert card.
- Verify your verified credential expert card. - Plan your verification solution Type: Docs Date: 2022-10-19
- Plan your issuance solution Type: Docs Date: 2022-10-19
- Azure AD Verifiable Credentials architecture overview (preview) Type: Docs Date: 2022-10-19 Tech: Entra
- Microsoft Entra Verified ID now generally available Type: Post Date: 2022-08-08 Tech: Entra
- Azure Active Directory Verifiable Credentials Type: Product Date: 2022-07-08 Tech: AzureAD
- Expanding the public preview of verifiable credentials Type: Post Founder: Ankur Patel Date: 2022-05-04 Standard: Verifiable Credentials
- Implement Compound Proof BBS+ verifiable credentials using ASP.NET Core and Mattr Parent: Personal Type: Post Founder: Damien Bowden Date: 2021-12-13
- Azure Active Directory VCs - preview introduction Parent: techmindfactory Type: Post Founder: Daniel Krzyczkowski Date: 2021-04-07 Tech: Entra
- DID Project - Azure Websites Type: Project Date: 2021-01-01 Standard: DID, Verifiable Credentials
- Decentralized identity Type: Product Date: 2019-06-18
- Why does standards certification matter? Type: Post Founder: Pamela Dingle Date: 2019-05-23 Standard: OpenID, FIDO, OpenID Connect
- Towards scalable decentralized identifier systems Type: Post Date: 2019-05-13 Standard: DID, Verifiable Credentials
DTDL is based on JSON-LD and is programming-language independent. DTDL isn’t exclusive to Azure Digital Twins, but is also used to represent device data in other IoT services such as IoT Plug and Play.
Find the languages and tools you need to develop on Azure.
Verifiable credentials help you build solutions that empower customers to manage their own data.
Strengthen security and reduce costs with Microsoft Entra
Hear Joy Chik, Microsoft Corporate Vice President for Identity, share the latest identity and access announcements in governance, workload identities, strong authentication, and new tools for upgrading from Active Directory Federation Services (AD FS) to Azure AD.
Microsoft Entra Verified ID is a decentralized identity solution that helps you safeguard your organization. The service allows you to issue and verify credentials. Issuers can use the Verified ID service to issue their own customized verifiable credentials. Verifiers can use the service’s free REST API to easily request and accept verifiable credentials in their apps and services. In both cases, you will have to configure your Azure AD tenant so that you can use it to either issue your own verifiable credentials, or verify the presentation of a user’s verifiable credentials that were issued by another organization. In case you are both an issuer and a verifier, you can use a single Azure AD tenant to both issue your own verifiable credentials as well as verify those of others.
Microsoft’s Microsoft Entra Verified ID (Azure AD VC) service enables you to trust proofs of user identity without expanding your trust boundary. With Azure AD VC, you create accounts or federate with another identity provider. When a solution implements a verification exchange using verifiable credentials, it enables applications to request credentials that aren’t bound to a specific domain. This approach makes it easier to request and verify credentials at scale.
This article covers the technical aspects of planning for a verifiable credential issuance solution. The Microsoft solution for verifiable credentials follows the World Wide Web Consortium (W3C) Verifiable Credentials Data Model 1.0 and Decentralized Identifiers (DIDs) V1.0 standards so can interoperate with non-Microsoft services. However, the examples in this content reflect the Microsoft solution stack for verifiable credentials.
Out of scope for this content is articles covering supporting technologies that aren’t specific to issuance solutions.
It’s important to plan your verifiable credential solution so that in addition to issuing and or validating credentials, you have a complete view of the architectural and business impacts of your solution. If you haven’t reviewed them already, we recommend you review Introduction to Microsoft Entra Verified ID and the FAQs, and then complete the Getting Started tutorial.
This architectural overview introduces the capabilities and components of the Microsoft Entra Verified ID service.
Customers rely on Azure AD to secure access to corporate resources. However, enabling use of credentials for utility beyond the company (e.g. prove employment for bank loan) is complex and comes with compliance risk. In contrast, identity documents from our everyday lives, like a driver’s license or passport, are well suited for utility beyond travel (e.g. age or residency). We believe an open standards-based Decentralized Identity system can unlock a new set of experiences that give users and organizations greater control over their data—and deliver a higher degree of trust and security for apps, devices, and service providers.
Verifiable credentials help you build solutions that empower customers to manage their own data.
more than 1,000 enterprises with premium subscriptions have issued and verified tens of thousands of verifiable credentials […] from remote onboarding at work, collaboration across business boundaries as well as enabling education beyond the campus […] we are extending the public preview […] for all Azure Active Directory (Azure AD) Free and Premium users.
This article shows how Zero Knowledge Proofs BBS+ verifiable credentials can be used to verify credential subject data from two separate verifiable credentials implemented in ASP.NET Core and Mattr. The ZKP BBS+ verifiable credentials are issued and stored on a digital wallet using a Self-Issued Identity Provider (SIOP) and OpenID Connect. A compound proof presentation template is created to verify the user data in a single verify
Once I discovered that documentation is available, I decided to create a small proof of concept. I have configured Verifiable Credentials accordingly to details in the documentation I have an existing Azure AD B2C tenant so it was much easier because users have to sign in first before they can be issued a verifiable credential.
Verify once, use everywhere. Join our list and we’ll let you know when our Public Preview is ready.
Discover the open standards-based solution for verified digital identity that gives people more control and convenience.
It’s a good month for identity certification at Microsoft! We are excited to have achieved two important goals: OpenID Certification for Azure Active Directory and also FIDO Certification for Windows 10. You may or may not know what these particular protocols do, but even if you don’t, it’s worth talking about what these certification programs accomplish.
Today, we’re announcing an early preview of a Sidetree-based DID network, called ION (Identity Overlay Network) which runs atop the Bitcoin blockchain based on an emerging set of open standards that we’ve developed working with many of our partners in the Decentralized Identity Foundation. This approach greatly improves the throughput of DID systems to achieve tens-of-thousands of operations per second
Meta
- Condatis revolutionizes staff management with Microsoft Entra Verified ID Related: Condatis Type: Testimonial Date: 2023-01-01 Standard: Verifiable Credentials
- Credivera Joins Microsoft Partner Network as Verifiable Credentials Provider Parent: Newswire CA Type: Press Date: 2022-07-26
- Announcing Azure AD Verifiable Credentials Type: Post Founder: Alex Simons Date: 2021-04-05 Standard: Verifiable Credentials
- Microsoft's Dream of Decentralized IDs Enters the Real World Related: At its Ignite conference today, Microsoft announced that it will launch a public preview of its “Azure Active Directory verifiable credentials” this spring. Parent: Wired Type: Post Date: 2021-03-02
- Decentralized digital identities and blockchain: The future as we see it Type: Post Founder: Alex Simmons Date: 2021-02-18 Tech: Entra
- Microsoft is quietly testing a project that aims to hand people complete control over their online data Parent: BusinessInsider Type: Post Founder: Isobel Asher Hamilton Date: 2019-01-04
- Decentralized digital identities and blockchain: The future as we see it Type: Post Founder: Alex Simons Date: 2018-02-12
- Partnering for a path to digital identity Related: ID2020 Type: Post Founder: Peggy Johnson Date: 2018-01-02
- Decentralized Identity Own and control your identity Type: Whitepaper Date: 2018
- Microsoft Building Open Blockchain-Based Identity System With Blockstack, ConsenSys Related: Blockstack, Consensys, ID2020, uPort Parent: BitcoinMagazine Type: Post Founder: GIULIO PRISCO Date: 2016-06-03 Tech: Bitcoin, Ethereum
At Edinburgh-based Condatis, as more employees transition from a hybrid work model to a full return to the office, they’re being greeted by a new, intuitive sign-in experience built on virtual, verifiable credentials that provide value-added access to office spaces and services. Whether someone is being onboarded, coming in as a temporary hire, or visiting a staff member, each person will see that some doors in the office will be open for them, and others won’t.
Credivera, a global leader in the secure, open exchange of verifiable credentials and digital identity solutions, today announced that it has joined the Microsoft Partner Network. In addition, it has been selected by Microsoft as a Microsoft Entra Verified ID solution provider. Credivera joins a list of internationally based companies in the Microsoft Partner Network who are leading the development of innovative digital identity tools, empowering individuals to completely own and control their unique digital identity.
We started on a journey with the open standards community to empower everyone to own and control their own identity. I’m thrilled to share that we’ve achieved a major milestone in making this vision real. Today we’re announcing that the public preview for Azure AD verifiable credentials is now available: organizations can empower users to control credentials that manage access to their information.
Beyond just controlling access, developers can further secure user data by encrypting that data using keys from their decentralized identifiers,’ a Microsoft spokesperson told WIRED in a statement. Based on such an approach, a bad actor may gain access to a system or datastore but can’t decrypt the data without keys that reside with individual user.’
Over the last 12 months we’ve invested in incubating a set of ideas for using Blockchain (and other distributed ledger technologies) to create new types of digital identities, identities designed from the ground up to enhance Personal privacy, security and control. We’re pretty excited by what we’ve learned and by the new partnerships we’ve formed in the process. Today we’re taking the opportunity to share our thinking and direction with you. This blog is part of a series and follows on Peggy Johnson’s blog post announcing that Microsoft has joined the ID2020 initiative. If you haven’t already Peggy’s post, I would recommend reading it first.
Foley reported that Bali’s “about” page described itself as a “new Personal data bank which puts users in control of all data collected about them… The bank will enable users to store all data (raw and inferred) generated by them. It will allow the user to visualize, manage, control, share and monetize the data.”
It also cited the concept of “inverse privacy,” a paper published by Microsoft researchers in 2014. It’s the idea that someone else has access to your online data, but you don’t.
Over the last 12 months we’ve invested in incubating a set of ideas for using Blockchain (and other distributed ledger technologies) to create new types of digital identities, identities designed from the ground up to enhance Personal privacy, security and control. We’re pretty excited by what we’ve learned and by the new partnerships we’ve formed in the process. Today we’re taking the opportunity to share our thinking and direction with you. This blog is part of a series and follows on Peggy Johnson’s blog post announcing that Microsoft has joined the ID2020 initiative. If you haven’t already Peggy’s post, I would recommend reading it first.
As discussions begin this week at the World Economic Forum, creating universal access to identity is an issue at the top of Microsoft’s agenda, and we think technology can be a powerful tool to tackle this challenge. It was last summer that Microsoft took a first step, collaborating with Accenture and Avanade on a blockchain-based identity prototype on Microsoft Azure. Together, we pursued this work in support of the ID2020 Alliance – a global public-private partnership dedicated to aiding the 1.1 billion people around the world who lack any legal form of identity. To say that we were encouraged by its mission would be an understatement. We were inspired by it.
Microsoft cloud identity systems already empower developers, organizations, and billions of people to work, play, and achieve more, but there’s so much more we can do to create a world where each of us, even in displaced populations, can pursue our life goals, including educating our children, improving our quality of life, and starting a business.To achieve this vision, we need to augment existing cloud identity systems with one that individuals, organizations, and devices can own so they can control their digital identity and data. This self-owned identity must seamlessly integrate into our daily lives, providing complete control over what we share and with whom we share it, and—when necessary—provide the ability to take it back. Instead of granting broad consent to countless apps and services and spreading their identity data across numerous providers, individuals need a secure, encrypted digital hub where they can store their identity data and easily control access to it.
The Microsoft strategist said that the Redmond, Washington, giant is working with Blockstack Labs and ConsenSys to leverage their current Bitcoin and Ethereum-based identity solutions, Blockstack and uPort. Through this open source collaboration, Microsoft and its partners intend to produce a cross-chain identity solution that can be extended to any future blockchains or new kinds of decentralized, distributed systems. In the coming weeks an open-source framework for developers will be made available on Azure.
Explainer
- Decentralized Identity: Verifiable Credentials Deep Dive Type: Post Founder: Pamela Dingle Date: 2022-12-09 Standard: Verifiable Credentials
- Decentralized Identity: The Basics of Decentralized Identity Type: Post Founder: Pamela Dingle Date: 2022-03-24 Standard: Verifiable Credentials, DID
- Why decentralization is the future of digital identities Type: Post Founder: Melanie Maynes Date: 2022-03-10
- The Direct Presentation model Type: Post Founder: Pamela Dingle Date: 2022-02-02
- The Five Guiding Principles for Decentralized Identities Type: Post Founder: Alex Simons Date: 2021-10-06
- Getting started with Self Sovereign Identity SSI Parent: Personal Type: Post Founder: Damien Bowden Date: 2021-03-29 Standard: Verifiable Credentials, DID
- Digital Identity, use Verifiable Credentials with Blockchain Parent: Office Garage IT Pro Type: Post Date: 2021-03-02
- What's New in Passwordless Standards, 2021 edition! Related: FIDO Type: Post Founder: Tim Cappalli Date: 2021-02-11 Standard: WebAuthN, CTAP
- 5 identity priorities for 2021—strengthening security for the hybrid work era and beyond Type: Post Founder: Joy Chik Date: 2021-01-28
- A Peek into the Future of Decentralized Identity Related: DIF Parent: IDPro Type: Paper Founder: Leo Sorokin Date: 2020-10-30 Standard: DID, Verifiable Credentials
- Decentralized identity explained Type: Video Date: 2020-08-14
To understand the world of verifiable credentials and verifiable presentations, you need to understand the ecosystem in which they are expected to be used. The VC Data Model v1.1 defines the roles different entities play in the data format, as well as two processes: credential issuance and credential presentation. You are probably familiar with a concept of issuers or verifiers in the physical world, but the role of holder could be new to you. The specification defines a holder as an entity that can “possess a verifiable credential and generate verifiable presentations”. Another way to think about this is the place you store your credentials until you are ready to take them out and use them for a purpose.
At the most basic level, decentralized identity is the story of three standardized documents: a proclamation, a letter of introduction, and an endorsement.
Turning credentials into digital form isn’t new, but decentralizing identity goes beyond that. It gives individuals the ability to verify their credentials once and use them anywhere as proof of attestation.
A credential is issued, and then held for a long period of time with intermittent voluntary presentations to many different verifiers.
Our goal in sharing these principles and our commitments is to help our customers, partners, and the decentralized identity community understand what motivates and guides us and how we think about this exciting opportunity.
Self-sovereign identity is an emerging solution built on blockchain technology for solving digital identities which gives the management of identities to the users and not organisations. It makes it possible the solve consent and data privacy of your data and makes it possible to authenticate your identity data across organisations or revoke it. It does not solve the process of authenticating users in applications. You can authenticate into your application using credentials from any trusted issuer, but this is vulnerable to phishing attacks. FIDO2 would be a better solution for this together with an OIDC flow for the application type. Or if you could use your credentials together with a registered FIDO2 key for the application, this would work. The user data is stored in a digital wallet, which is usually stored on your mobile phone. Recovery of this wallet does not seem so clear but a lot of work is going on here which should result in good solutions for this. The credentials DIDs are stored to a blockchain and to verify the credentials you need to search in the same blockchain network.
a special edition of Microsoft Mechanics with Microsoft’s Identity CVP Joy Chik, to cover a brand new solution called Verifiable Credentials that uses blockchain-based underpinnings and cryptographic keys to ensure that you’re in control of your own identity online
The Web Authentication API (WebAuthN) Level 2 specification is currently a Candidate Recommendation at the W3C. “Level 2” essentially means major version number 2. The version 2.1 of the Client to Authenticator Protocol (CTAP) specification is a Release Draft at the FIDO Alliance.
In this paradigm, individuals can verify a credential with an ID verification partner once, then add it to Microsoft Authenticator (and other compatible wallets) and use it everywhere in a trustworthy manner.
As digital transformation sweeps across the globe, it has affected everyone – from citizens to employees, from corporations to governments. Digital identity is a foundational enabler for business processes in the digital economy. Decentralized identity is the next evolution of digital identity capabilities and brings with it an opportunity to streamline how people interact with other institutions, physical objects, and with one another. This paper considers the future world of decentralized identity and offers clarity around the benefits of decentralized identity, terminology, sample scenario, and a sample technical implementation, while also addressing some of the limitations of this model. This paper further grounds the reader in the current state of decentralized identity capabilities while outlining the evolution of identity practices from past to present.
What is decentralized identity? How does it give you more control over your digital identity and keep your information on the internet safer? This video explains in short what decentralized identity is and how it can replace usernames and passwords to verify you are who you say you are quickly and easily.
Standards
- Introduction to the future of identity - DIDs & VCs Parent: XT Seminars Type: Post Date: 2022-03-02
- Challenges to Self Sovereign Identity Related: Trinsic, Mattr, Evernym Parent: Personal Type: Post Founder: Damien Bowden Date: 2021-10-11 Market: Critique
- Why WebAuthN will change the world Type: Post Founder: Pamela Dingle Date: 2019-04-19 Tech: Javascript Standard: WebAuthN
- To Understand WebAuthN, Read CredMan Type: Post Founder: Pamela Dingle Date: 2019-02-15 Standard: WebAuthN, CredMan
- All about FIDO2, CTAP2 and WebAuthN Type: Post Founder: Pamela Dingle Date: 2018-11-20 Standard: FIDO2, CTAP2, WebAuthN
In this blog, I want to start by thinking about identity in general and then explaining Decentralized Identifiers (DIDs) and Verifiable Credentials (VCs). I will show you how you can issue your own DIDs and VCs using the new Microsoft service in future blogs. This series’ final blog will look at how DIDs can be anchoPred in decentralized transaction ledgers using ION and the Bitcoin blockchain.
Authentication using SSI credentials would have to same level of security as the authenticator apps which you have for existing systems. This is not as safe as using FIDO2 in your authentication process as FIDO2 is the only solution which protects against phishing. The SSI Authentication is also only as good as the fallback process, so if the fallback process, recovery process allows a username or password login, then the level would be passwords.
With WebAuthN, any web entity can call a simple Javascript API and ask for a cryptographically secure credential. What happens next is pretty cool – the world’s browsers have worked with the world’s operating system makers and the world’s hardware manufacturers, so that when a website asks for a credential, the browsers work with the underlying platform to securely locate compliant local hardware and talk to it!
take a cruise through the W3C Credential Management (aka CredMan) specification first. CredMan sets up the object model for the Credential object model that WebAuthN’s PublicKeyCredential extends.
To understand how FIDO2 authenticators work, you need knowledge of two specifications in two different standards bodies. The WebAuthentication (aka WebAuthN) spec lives at W3C (where the browser makers meet) while the Client-to-Authenticator (aka CTAP2) spec lives at the FIDO Alliance (where hardware and platform folks have joined to solve the problem of Fast IDentity Online).
Howto
- Create and issue verifiable credentials in ASP.NET Core using Azure AD Parent: Personal Type: Post Founder: Damien Bowden Date: 2021-10-25
- Issuing your own DIDs & VCs with Azure AD Parent: XT Seminars Type: Post Date: 2021-06-01 Tech: Entra, AzureAD
- Verify Vaccination Data Using Zero Knowldege Proofs with ASP.Net Core and Mattr Related: Mattr Parent: Personal Type: Post Founder: Damien Bowden Date: 2021-05-31 Tech: ASP.NET Standard: Verifiable Credentials
- Present and Verify Verifiable Credentials in ASP.NET Core using Decentralized Identities and Mattr Related: Mattr Parent: Personal Type: Post Founder: Damien Bowden Date: 2021-05-10 Tech: ASP.NET
- Create an OIDC credential Issuer with Mattr and ASP.NET Core Related: Mattr Parent: Personal Type: Post Founder: Damien Bowden Date: 2021-05-03 Tech: ASP.NET
- Verifying Verifiable Credentials in ASP.NET Core for Decentralized Identities using Trinsic Related: Trinsic Parent: ML-Software Type: Post Founder: Matteo Locher Date: 2021-04-13
- Creating Verifiable credentials in ASP.NET Core for decentralized identities using Trinsic
Related: Trinsic
Parent: Personal
Type: Post
Founder: Damien Bowden
Date: 2021-04-05 Tech: QR Code Standard: DID
This article shows how Azure AD verifiable credentials can be issued and used in an ASP.NET Core application. An ASP.NET Core Razor page application is used to implement the credential issuer. To issue credentials, the application must manage the credential subject data as well as require authenticated users who would like to add verifiable credentials to their digital wallet. The Microsoft Authenticator mobile application is used as the digital wallet.
This article shows how Zero Knowledge Proofs ZKP verifiable credentia can be used to verify a persons vaccination data implemented in ASP.NET Core and Mattr. The ZKP BBS+ verifiable credentials are issued and stored on a digital wallet using a Self-Issued Identity Provider (SIOP) and Open ID Connect. The data can then be used to verify if the holder has the required credentials, but only the required data is used and returned to the verification application.
This article shows how use verifiable credentials stored on a digital wallet to verify a digital identity and use in an application. For this to work, a trust needs to exist between the verifiable credential issuer and the application which requires the verifiable credentials to verify. A blockchain decentralized database is used and Mattr is used as a access layer to this ledger and blockchain. The applications are implemented in ASP.NET Core.
Whilst in Damien’s blog post he showed how a verifiable credential can be issued to a so called credential holder, this blog post will be about how we can verify such credentials as part of a business workflow. After an issuer has issued credentials to the holder and they have stored these into their wallet, a verifier can now ask a holder to verify them self with a certain credential. A verifier can add policies to check for certain attributes but also add restrictions like a specific issuer DID. With this in place a verifier can create a verification request which will be sent to the credential holder. This step is very important because it is where a cryptographic challenge is generated that the holder must respond to. This guarantees that the holder is responding to exactly this specific verification request. After the verification request gets returned to the verifier, it needs to be verified against the ledger to make sure it is valid. The verification record does not only contain the attributes, but also some metadata such as the digital signature of the issuer of the credentials, revocation details, verification policies etc. which then get validated against their sources. The image below describes this trust-triangle between the issuer, holder and verifier.
In this part we are going to look at how we can verify these credentials in order to continue some sort of business process. We will continue with the sample that Damien started and after obtaining our driver license we want to sign up for a new insurance. But we can only sign up at this insurance company if we can deliver proof of our driver license.
The National Driving license application is responsible for issuing driver licenses and administrating licenses for users which have authenticated correctly. The user can see his or her driver license and a verifiable credential displayed as a QR code which can be used to add the credential to a digital wallet. When the application generates the credential, it adds the credential DID to the blockchain ledger with the cryptographic proof of the issuer and the document. When you scan the QR Code, the DID will get validated and will be added to the wallet along with the request claims. The digital wallet must be able to find the DID on the correct network and the schema and needs to search for the ledger in the correct blockchain. A good wallet should take care of this for you. The schema is required so that the data in the DID document can be understood.
Related
From other pages on this site. (Beta)
- Name: Decentralized Identifiers Market May See a Big Move: Major Giants- Consensys, Blockstack, Danube Tech
Parent: Xaralite Type: Report Related: Transmute, Consensys, uPort, IBM, Blockstack, Danube Tech, Trinsic, Spherity, Microsoft Related: Transmute, Consensys, uPort, IBM, Blockstack, Danube Tech, Trinsic, Spherity, Microsoft, - Name: Transmute
Type: Company Author(s): Eric Olszewski, Karyl Fowler, Orie Steele Related: DIF, DHS, Microsoft, Consensys, Oracle Date: 2017-05-01 Related: DIF, DHS, Microsoft, Consensys, Oracle, Location: USA, Texas, Austin, Sector: Enterprise Industry: Supply Chain Projects: VCI Tech: Ethereum Standard: DID, Verifiable Credentials, OAuth, OIDC, - Name: Introducing Element
Parent: Transmute Type: Post Related: Microsoft, Consensys, DIF Date: 2019-05-10 Related: Microsoft, Consensys, DIF, Tech: Ethereum Standard: DID, IPFS, Sidetree, Element,
provides valuable market size data for historical (Volume & Value) from 2016 to 2020 which is estimated and forecasted till 2026*. Some are the key & emerging players that are part of coverage and have being profiled are Transmute (United States), Consensys (United States), uPort (United States), IBM (United States), Tykn Tech (Netherlands), Blockstack (United States), Danube Tech (Austria), Trinsic (United States), Spherity (Germany), Microsoft (United States).
Build a network of trust with Transmute
Transmute secures critical supplier, product, and shipment data to give customers a competitive edge in the increasingly dynamic global marketplace.
Transmute is excited to announce Element, an implementation of the Sidetree Protocol on top of Ethereum and IPFS. This work was done in collaboration with Microsoft and Consensys under the Decentralized Identity Foundation (DIF)