System Architecture and Self Sovereign Identity
General
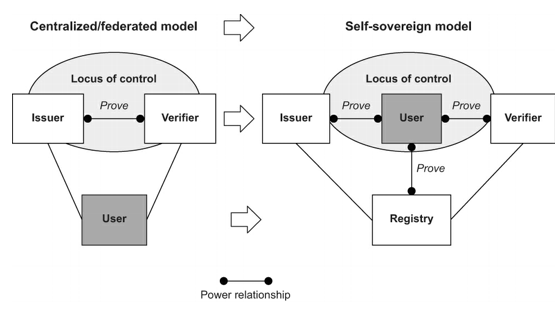
- Centralized\Federated vs Self Sovereign 2022-08-29 dominiumssi
Anyone who wants to understand DID and Self Sovereign Identity should begin by understanding the graph below. We are shifting the power from the companies to the users. That’s it in a nutshell.
- Good Welfare, Bad Platforms?: The Risks of Centralized Digital Identity Systems 2022-02-02 OpenID
As S. Shakthi and I noted in a recent research paper, digital identity systems are widely seen as datafiers by virtue of their core property of reducing the person to machine-readable data. A datafier is a system that performs the crucial operation of converting the physical into digital. A different, contrasting view is also emerging in research: digital identity systems are increasingly seen as platforms, i.e. “technological building blocks” on which different types of complements can be constructed.
- Leveraging the Identity Metasystem 2021-12 Phil Windley
the metasystem guarantees the fidelity of the credential exchange. Credential fidelity comprises four important attributes. Credential exchange on the identity metasystem:
- Reveals the identifier of the issuer
- Ensures the credential was issued to the party presenting it
- Ensures the credential has not been tampered with
- Reveals whether or not the credential has been revoked
- Token-Based Identity 2021-10 Phil Windley
Token-based identity systems move us from talking about who, to thinking about what, so that people can operationalize their digital lives. Token-based identity systems support complex online interactions that are flexible, ad hoc, and cross-domain.
- The Basic Building Blocks of SSI 2020-07-29 Drummond Reed, Alex Preukschat Manning
In many cases these core concepts have been established for decades. What’s new is how they’re put together to create a new model for digital identity management. The purpose of this article is to quickly familiarize you with these seven basic building blocks from a conceptual and technical point-of-view.
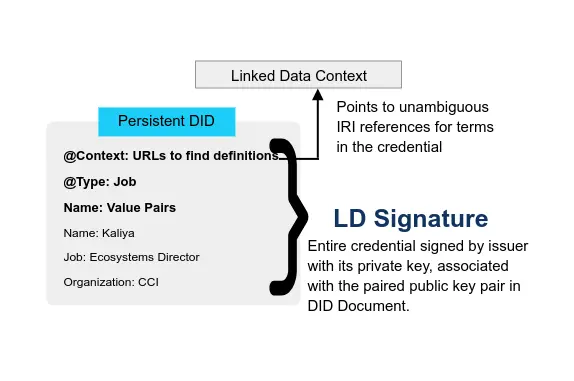
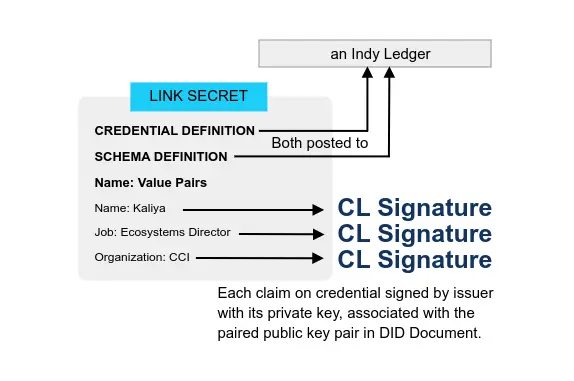
- Verifiable credentials (aka digital credentials)
- Issuers, holders, and verifiers
- Digital wallets
- Digital agents and hubs
- Decentralized identifiers (DIDs)
- Blockchains
- Governance frameworks (aka trust frameworks)
- Your User is Your API 2021-05-17 Evernym
The customer becomes the integration point. The customer is the API. Rather than having one huge, expensive, and probably illegal data hub, every customer becomes a data hub in their own right. They provide the data needed, just-in-time, under their control.
- The Unbundling of Authentication vs Authorization - What You Need to Know 2021-09-08 Ping Identity
Authentication and authorization are both processes that fall under the category of identity and access management (IAM), but they serve different purposes.
- The Buzz Behind Zero Trust 2021-10-21 State of Identity
The Zero Trust model is the belief that no one should be trusted from inside or outside your network, until their identity has been verified. Zero trust refers to the alignment of maturing identity practices, an established understanding of user behaviors, and the application of least-privilege access security policy decisions to trust boundOaries
- What Is Zero Trust? 2021 Ping
- The network is always assumed to be hostile.
- External and internal threats exist on the network at all times.
- Network locality is not sufficient for deciding trust in a network.
- Every device, user and network flow is authenticated and authorized.
- Policies must be dynamic and calculated from as many sources of data as possible.
- Compare and Contrast — Federated Identity vs Self-sovereign Identity 2021-04-26 Affinidi
The next step was a federated form of identity where third parties issued digital identity credentials using which users could log into other websites or services. Typically, these were your Google and Facebook logins. In the process, these third parties that issued federated identities became the middlemen.
- The SSO Practitioner’s Introduction to Decentralized Identity 2020-10-13
Written for IAM professionals familiar with federations.
In most self-sovereign and decentralized identity systems the trust model is fundamentally unidirectional, where a verifier will trust the issuer, but the issuer may have no knowledge of the verifier.
- The Architecture of Identity Systems 2020-09 Phil Windley
We can broadly classify identity systems into one of three types based on their architectures and primary root of trust:
- Administrative
- Algorithmic
- Autonomic
- Never mind who I am, ask me about my credentials 2020-02-09 John Phillips
Many (most) identity systems make a fundamental assumption that is built into their very architecture. This assumption creates three significant problems: privacy erosion; toxic data stores; and poor security.
- Decentralized Identity Trilemma 2018-08-13 Maciek Laskus
- Self-sovereignty — anybody can create and control as many identities1 as they wish without 3rd party involvement.
- Privacy-preserving — one can acquire and utilize an identifier without revealing their ‘real name’ or other personality identifying information.
- Sybil-resistant — identity is subject to scarcity; i.e., creating more identifiers cannot be used to manipulate a system2.
- Self-Sovereign vs Administrative Identity 2012-03-25 Doc Searls
The problem I’m trying to surface here is that we need full respect for self-sovereign identities, and identifiers, before we can solve the problem of highly fractured and incompatible administrative identifiers — a problem that has only become worse with the growth of the Web, where by design we are always the submissive and dependent party: calves to administrative cows.
Decentralized Public Key Infrastructure DPKI
- Decentralized Public Key Infrastructure 2015-12-24 rwot1
Today’s Internet places control of online identities into the hands of third-parties. Email addresses, usernames, and website domains are borrowed or “rented” through DNS, X.509, and social networks. This results in severe usability and security challenges Internet-wide. This paper describes a possible alternate approach called decentralized public key infrastructure (DPKI), which returns control of online identities to the entities they belong to. By doing so, DPKI addresses many usability and security challenges that plague traditional public key infrastructure (PKI). DPKI has advantages at each stage of the PKI life cycle. It makes permissionless bootstrapping of online identities possible and provides for the simple creation of stronger SSL certificates. In usage, it can help “Johnny” to finally encrypt thanks to its relegation of public key management to secure decentralized datastores. Finally, it includes mechanisms to recover lost or compromised identifiers.
Related
- SCPKI: A Smart Contract-based PKI and Identity System
- KeyChains: A Decentralized Public-Key Infrastructure
- ClaimChain: Decentralized Public Key Infrastructure
- A Decentralized Public Key Infrastructure with Identity Retention
- Privacy based decentralized Public Key Infrastructure (PKI) implementation using Smart contract in Blockchain