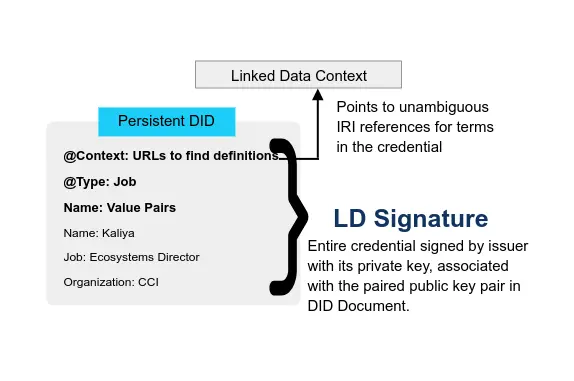
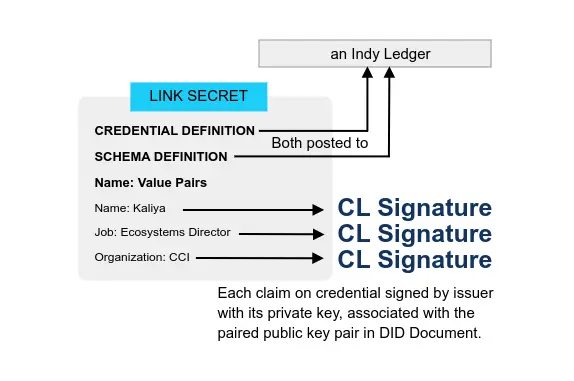
User Experience and Self Sovereign Identity
General
- Identity and Consistent User Experience 2021-11 Phil Windley
There’s a saying in security: “Don’t roll your own crypto.” I think we need a corollary in identity: “Don’t roll your own interface.” But how do we do that? And what should the interface be? One answer is to adopt the user experience people already understand from the physical world: connections and credentials.
- Fluid Multi-Pseudonymity 2021-09-07 Windley
Fluid multi-pseudonymity perfectly describes the way we live our lives and the reality that identity systems must realize if we are to live authentically in the digital sphere.‘
- Humanizing PoSSI- Human-centric structure of the Principles of SSI 2021-05-06 Line Kofoed
- [Line] Welcome and introductions; background information around how this topic is important to discuss
- Principles of SSI - https://sovrin.org/principles-of-ssi/
- Sovrin Foundation is working on Sovrin Utility GF and the Sovrin Ecosystem GF
- Work on the SEGF led to reviewing how we define an ecosystem (see slide for definition) → identity ecosystem for identity services
- The approach to grouping the 12 principles are intended to enable better understanding as digital trust ecosystems grow
- Ecosystem of ecosystems will need a foundational set of values and principles and the PoSSI
- [Sterre] It is good to have the order the principles to help better understanding
- [Drummond] additional supplementary material to help laypersons understand the PoSSI better
- [Alex] is the original sequence/numbering sufficient and complete?
- [Chris] the grouping is more important for the SEGF
- [please join Sovrin meetings]
- Bringing User-Centricity to Decentralized Identity 2021-08-01 Nat Sakimura KuppingerCole
Raj Hegde sits with identity veteran, Nat Sakimura - Chairman of OpenID Foundation to understand how user-centric learnings from existing authentication protocols can be applied to future identity initiatives.
- How humans understand identity 2021-07-09 Universal Identity
Lack of great user experiences is often raised as one of decentralized identity’s (and public blockchain’s) missing ingredients for ubiquitous adoption. However to arrive at usable experiences across the industry, we first need to reach consensus around basic user personas and mental models, then design and build interoperable system accordingly.
Relationship based Identity
- Are Transactional Relationships Enough? 2022-03 Phil Windley
Our online relationships are almost all transactional. A purely transaction digital life can’t feel as rich and satisfying as one based on interactional relationships. As more of our relationships are intermediated by technology, finding ways to support interactional relationships will allow us to live authentic digital lives.
- Backchannel: A relationship-based digital identity system 2021-09 Ink and Switch
Using Backchannel as a model example, we propose four design principles for trusted digital relationships. Then we used Backchannel to design and build three sample apps: chat, location sharing, and document preview. We also tested these designs with journalists, researchers, and designers. Based on this testing, we outline common user experience challenges and recommended solutions.
- Authentic Digital Relationships 2020-08 Phil Windley
Self-sovereign identity (SSI) systems offers an alternative model that supports richer relationships. Rather than provisioning identifiers and accounts in an administrative system where the power imbalance assures that one party to the relationship can dictate the terms of the interaction, SSI is founded on peer relationships that are co-provisioned by the exchange of decentralized identifiers. This architecture implies that both parties will have tools that speak a common protocol.
- Relationships and Identity 2020-07 Phil Windley
We build digital identity systems to create and manage relationships—not identities.
Customer Relationships
- The Identity Imperative: Risk Management, Value Creation, and Balance of Power Shifts 2021-12-10 Michael Becker IdentityPraxis
Brands need to prepare for fundamental shifts in people’s attitudes and expectations. The implications of these shifts will be profound, as they will force a change in competition, business models, product offerings, and business practices.
- The 7 Deadly Sins of Digital Customer Relationships 2021-03-02 Evernym
It’s not just about measuring customers, it’s about keeping them. Yet the more I look at how businesses design and manage their relationships with customers, the more I see dysfunction, waste and a collapse of consumer trust. In fact, I see a number of core business behaviours that are causing this waste, this dysfunction. Seven to be precise.
- Decentralized Identifiers: Building Smarter, More Sustainable Customer Relationships 2021-03-02 Evernym
DIDs are about building lasting private and secure digital relationships with customers, and as we’ll see with each of the Deadly Sins, about reducing costs, increasing compliance and enabling truly personalized products and services – without being creepy.
Design
- More security does not have to mean less user-friendliness 2022-06-05 Martin Kuppinger, Tagesspiegel
The passwords that have been declared dead are far from dead. Nevertheless, the way in which users authenticate themselves is changing towards more security and convenience.
- How Might we Design Consent Experiences for Data Sharing? 2022-05-27 ToIP HXWG Arianna Rossi, Xengie Doan, Interdisciplinary Center for Security, Reliability and Trust (SnT) at the University of Luxembourg
The complex ecosystem where manifold transactions can be automatically enabled by smart contracts contributes, at least in principle, to establish greater transparency about data use towards the many parties involved. However, the mere fact of building such a verifiable and traceable architecture does not automatically translate into understandable communications, easily applicable instructions and smooth transactions for human beings.
- Tap and Prove 2021-07-15 Stephen Wilson
We should be able to “tap and prove” any important fact and figures about ourselves – as easily as we tap and pay with a mobile phone at any one of 100s of millions of terminals globally.
- Disability-inclusive ID Systems 2020-12-09 World
Creating an inclusive ID system requires a comprehensive, whole-of-system approach to overcome barriers to ID enrollment and use for persons with disabilities.
- EPS for SSI (Self-Sovereign Identity) 2020-08-15 Hitoshi Kokumai
you might be interested to hear that the core of EPS is designed to convert images to high-entropy codes, which work as very long passwords and also as the seeds of symmetric or asymmetric cryptographic keys.
- Falsehoods Programmers Believe About Names - With Examples 2018-01-08 Shine Solutions Group
In this post I’m going to list all 40 of Patrick’s original falsehoods, but give you an example (or two) drawn from my experiences working in this space. Ready? Let’s go!
- People have exactly one canonical full name.
- People have exactly one full name which they go by.
Trust
- An Introduction to Digital Trust 2021-09-06 Northern Block
what’s the purpose of SSI? It’s about enabling Digital Trust (which is quickly becoming an integral part of digital transformation for organizations).
- Will users and organizations have trust in keys roaming via the cloud? 2022-05-12 Kuppinger Cole EIC2022
the FIDO Alliance, a set of open, scalable, and interoperable specifications has been developed to replace passwords as a secure authentication method for online services. The alliance has also worked with companies such as Microsoft, Google, and Apple to integrate and adopt FIDO standards across their operating systems.
Users Needs
- People Don’t Understand the Purpose of Privacy Policies and Terms of Service – New Research Published 2022-01-24 Me2B Alliance (Report
- Consumers are aware that legal policies exist on connected technologies and that they should read them, but they continue to choose to largely ignore them.
- 55% of survey participants did not understand that a TOS/TOU agreement is a legal contract. This has significant implications because a key requirement for legally binding contracts is mutual assent, which means that both parties have a “meeting of the minds” and must understand they’re entering into a contract.
- None of the interview participants were aware of tools that explain or rate privacy policies and TOS/TOU documents, and half said that a score would not change their behavior.
- 66% of survey respondents believe that privacy policies protect the business, while 50% say they protect the consumer. It’s questionable that privacy policies protect either the individual or the business, as they are primarily legal notices, disclosures of how data is used by the technology and the companies behind it. Moreover, 39% of respondents erroneously thought that the privacy policy was a contract [between them and the company].
- What Your Customers Really Want From Your Login Box 2021-10-06 Auth0
customers want convenience and control: they want to choose which authentication method to use – whether it’s MFA or SSO or biometrics. They want a brand experience that resembles a concierge desk: a 24/7 service where no demand is too big. To top it off, they don’t want to see any technical glitches
Location Tracking
- Most People Feel Negatively About Location Tracking in Websites and Apps 2021-11-16 Me2Ba
The Spotlight Report, “Consumer Sensitivity to Location Tracking by Websites and Mobile Apps”, was developed to validate the Location Commitment scoring criteria in the Me2B Alliance Validation Research: Consumer Sensitivity to Location Tracking by Websites and Mobile Apps
- What is Respectful Use of Location Information? New Me2BA Reearch 2021-11-22 Me2B
As we’ve been performing independent product audits over the past year and a half, we received some push-back on our passing criteria related to the automatic translation of IP address to geographic location. Vendors felt that automatically calculating the user’s geographical location was, in fact, a benefit. However, in our specification, that behavior will receive a failing score. At an impasse, we decided to conduct some validation testing with Me-s.
- “Spotlight Report #3: Consumer Sensitivity to Location Tracking by Websites and Mobile Apps” 2021-11-16 Me2B
This research quantifies and qualifies public opinion of location tracking in a variety of different contexts within web and mobile technology.
- Do Consumers Even Want Personalized Ads? 2021-06 Anonyme
The YouGov poll of consumers in France and Germany we mentioned earlier says it’s the behind the scenes or back door nature of personalization that gives people the creeps.
- Only 5% Of US Consumers Want To Be Tracked For Ads 2021-05 Anonyme
That means 95% of US consumers are saying ‘no way’ to cross-app tracking with Apple’s new App Tracking Transparency (ATT) feature.